Spring Security is a very powerful framework in the Spring family for authentication and permission control, and we can easily extend it to meet our current system security requirements.
However, compared with some other technologies such as JPA, Spring Security is more difficult to get started. Many people can hardly write a Demo independently after reading video or sending documents, so they may give up learning this thing later.
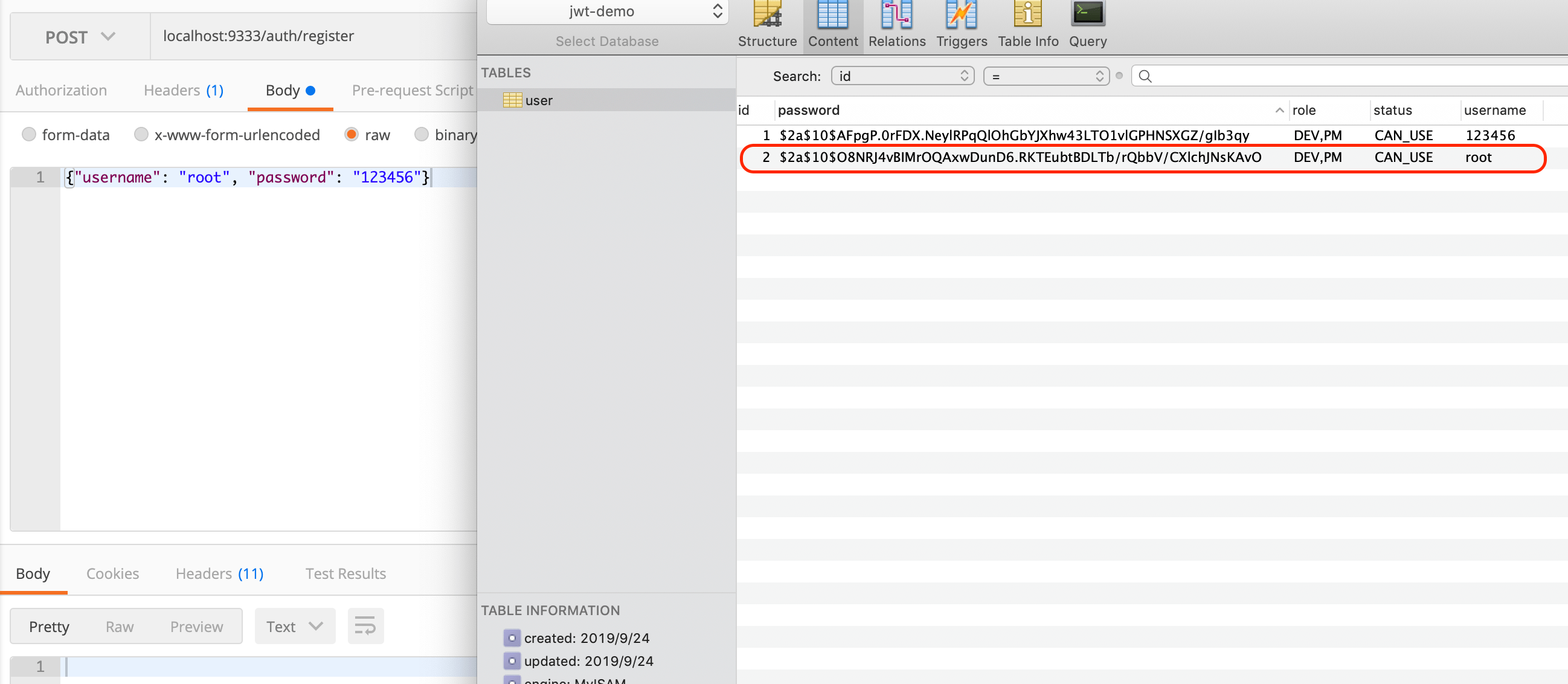
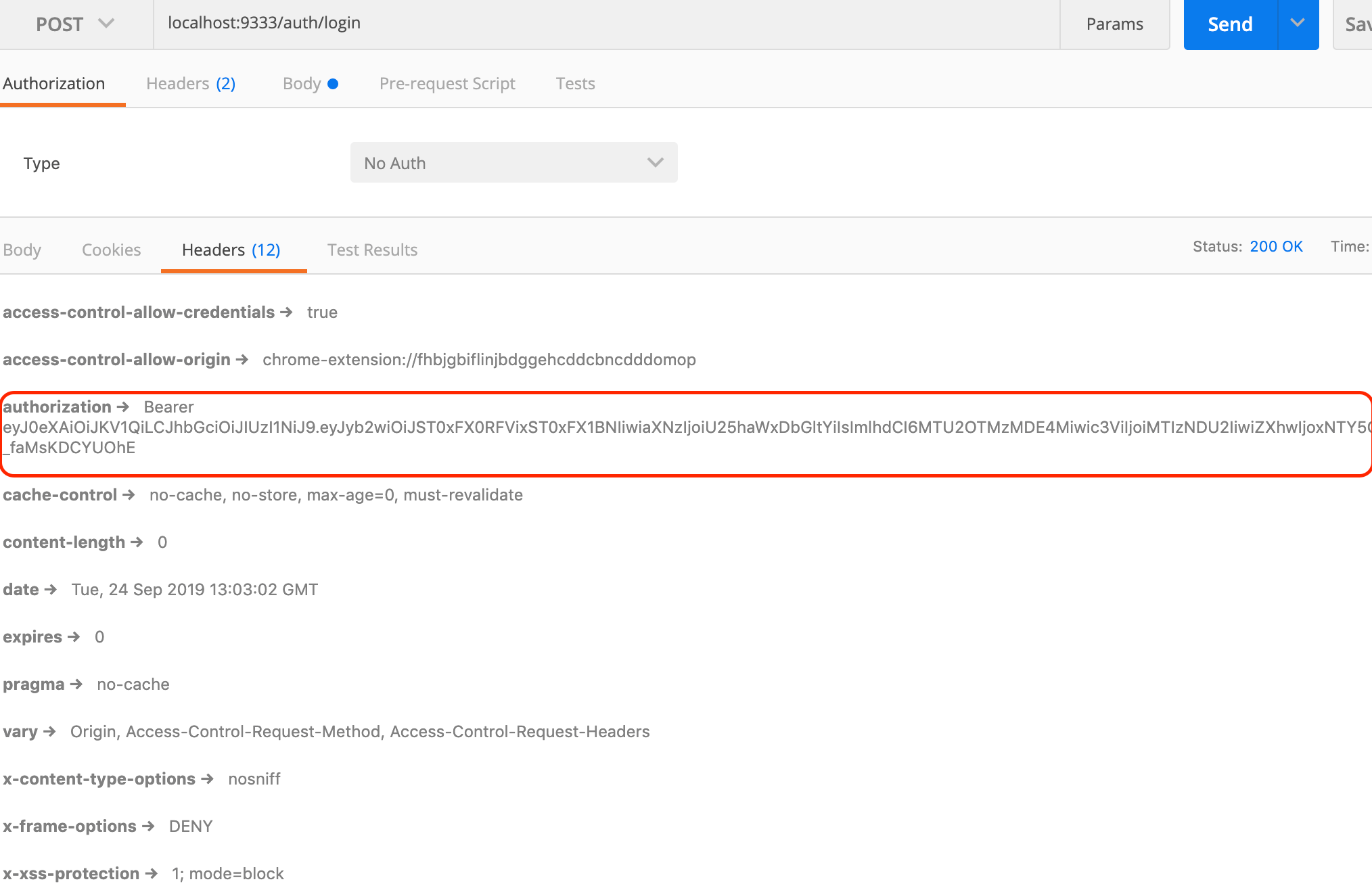
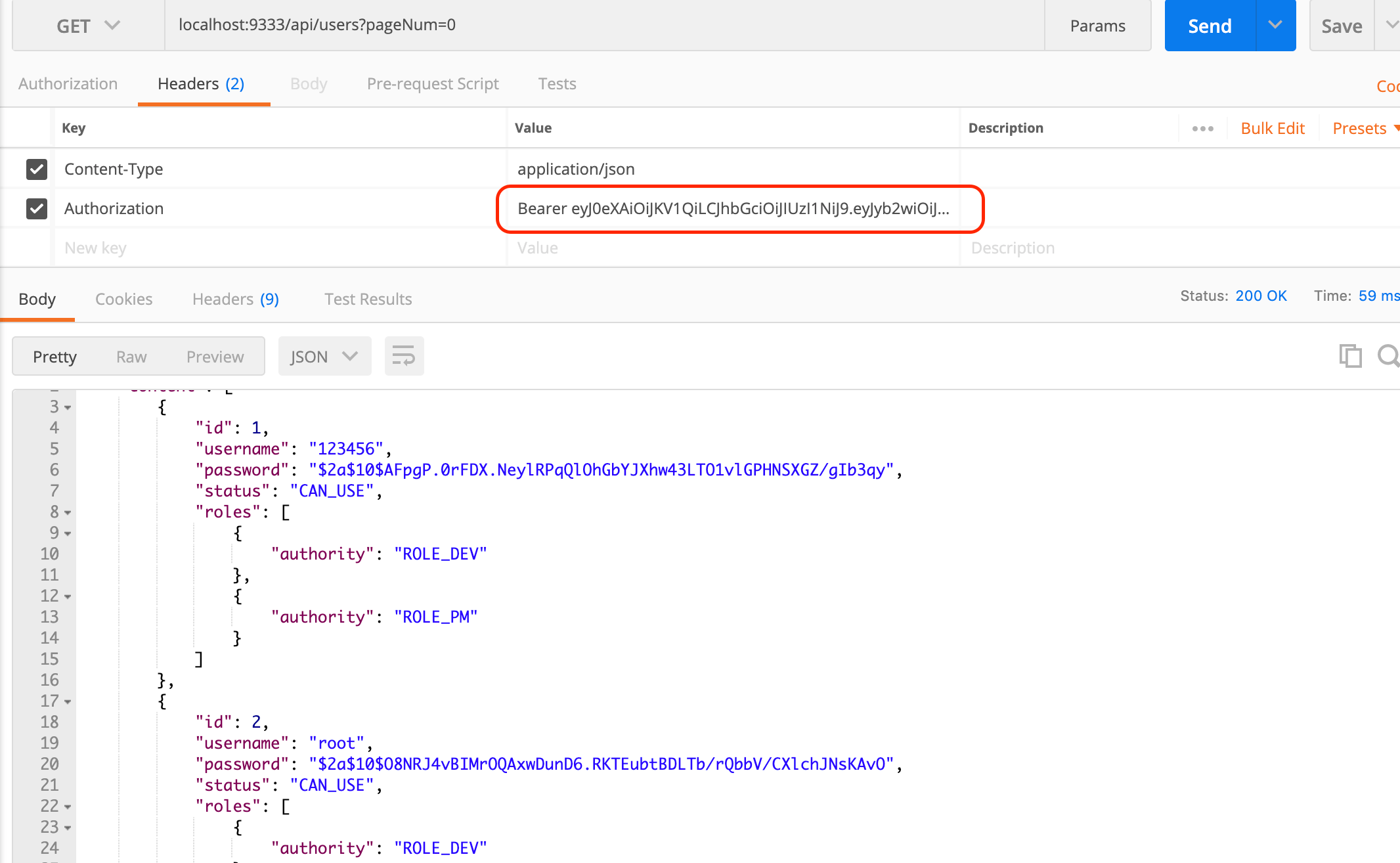
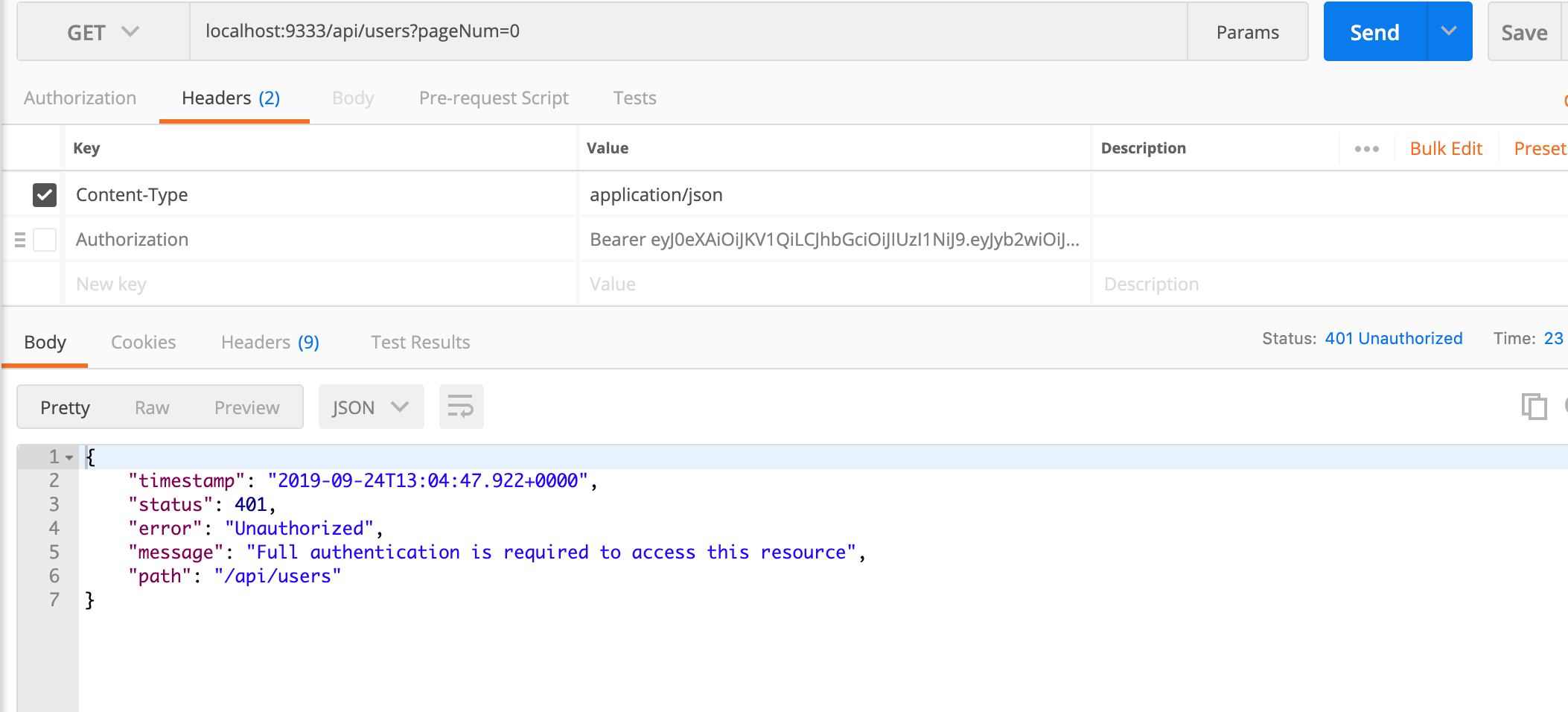
Spring Security, a powerful Security authentication framework, has been used in the induction training practical project when I first came to the company and the projects I am working on now. It can be seen that this framework is a good choice in the field of authentication and permission authentication. I am not familiar with Spring Security because I did not make this part of the module of the previous project by myself. So I took the time to learn this part of knowledge and implemented a simple Demo. This Demo mainly USES Spring Security and Spring Boot, and all the dependencies adopt the latest stable version. Beyond the initial project, the JPA technology was also used. The code structure of the project is as follows (chrome plug-in: octree), which is relatively clear as a whole. Due to my limited ability and time, there must be a lot of areas that can be optimized. Interested friends can improve it together.
- git clone https://github.com/Snailclimb/spring-security-jwt-guide.git
- open project and wait maven to install project Dependencies
- change
application.propertieschange the database connection information parameter to your own - Run the project (related data tables will be created automatically, if you don't understand, take a look at JPA)