-
Notifications
You must be signed in to change notification settings - Fork 1.2k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Simplify authentication and authorization with a more flexible and lightweight approach #19182
Comments
|
@skabashnyuk @metlos according to @davidfestal kube-rbac-proxy does "almost but not quite" do what we need... But it certainly should be a good starting point @davidfestal Yeah, I was mainly thinking of a mix of 1. kube-rbac-proxy and 2. oauth2-proxy.
in https://github.com/brancz/kube-rbac-proxy/tree/master/examples/oidc |
|
First jumboard we have after internall call with platform team |
|
We have these entrypoints to Che, that has to be authenticated (considering single-host deployment with devworkspaces)
|
|
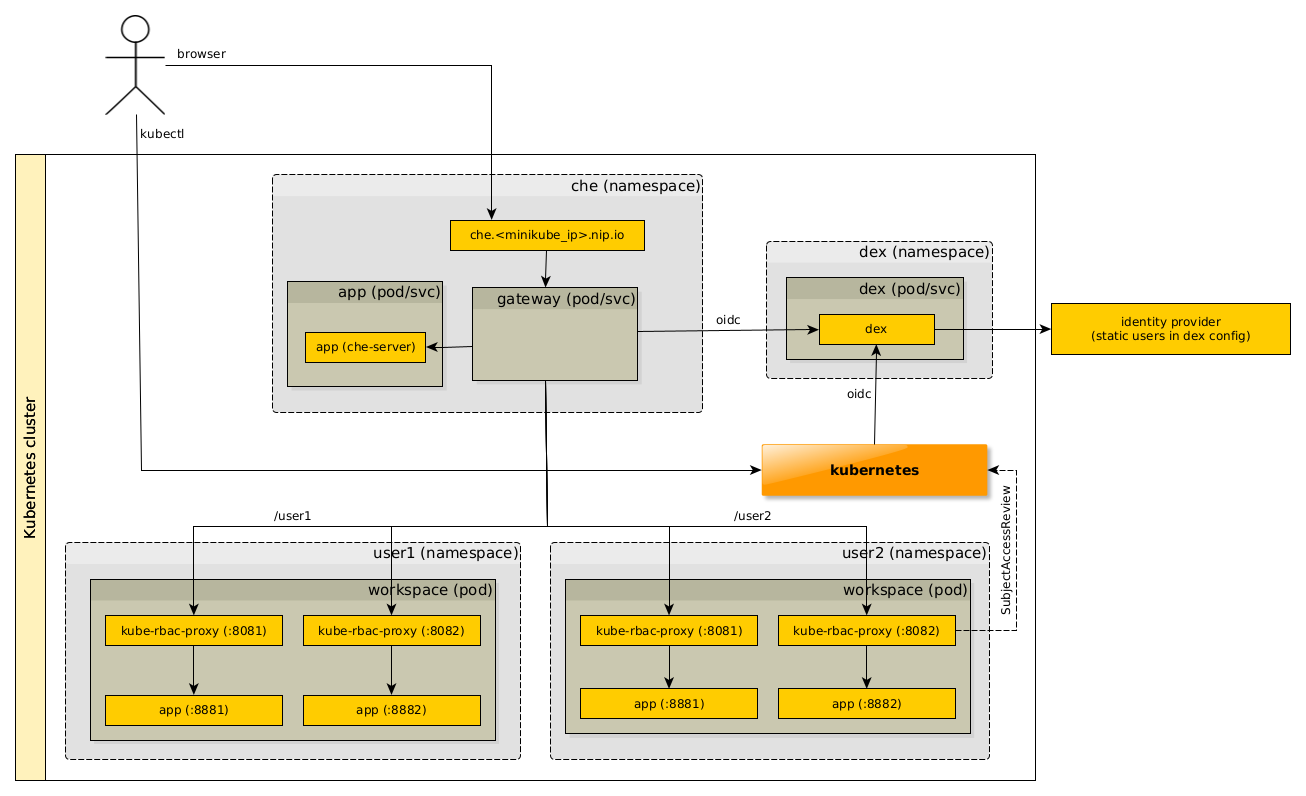
We've prepared POC on minikube for "single-host" routes. See https://github.com/che-incubator/che-auth-playground/tree/master/kubernetes for the setup: There are some issues/unanswered questions:
|
Status updateStep 1 - Foundations (Che 32?)We've starting working on implementation. We're now focusing only on OpenShift with DevWorkspaces.
After these 3 we'll have an option to install Che on OpenShift without Keycloak and any OpenShift user will be able to login to Che and use DevWorkspaces (no devfile v1 support). Step 2 - Workspace authentication (subpath) (Che 34?)We will then focus on workspace authentication. At first, we'll secure subpath endpoints ([che-auth] - secure workspace subpath endpoints in new auth gateway #19707). ❗ Concern/complicationThere is one concern about this! For new authentication, we need to change the deployment of the che-gateway. Currently it's "only" routing the traffic, but with new auth it will be responsible also for authentication and authorization. We now have 2 che-gateways (Traefik):
Eech gateway has it's own Route -> devworkspaces have different hostname than che-server or devfile v1 workspace. We're currently in the process of merging these 2 operators together and having only one gateway and one Route. Ideally, we would implement workspace authentication AFTER this merger is done. Otherwise we would have to implement same functionality twice (in che-operator and devworkspace-che) and it might get complicated due to different hostname and cookies path (not verified). Future (Che X)
|
|
moving issue to 7.42 milestone as this issue is part of the endgame |
|
scope of this epic is complete and all issues are close. I'm closing this. Following issues/improvements will be solved in dedicated issues. |


Is your task related to a problem? Please describe.
We would like to revise the way how we do authentication and authorization in Eclipse Che.
Requirments
Problems that we currently have with Keycloak:
Describe the solution you'd like
Something like OAuth2 proxy looks like the ideal solution
Dex, rbac-proxy and OpenShift OAuth need to be evaluated as well
Implementation
[che-auth] - subdomain (a.k.a. multi-host) routes auth #19550[che-auth] Che with Devworkspaces should be able to use Dex as identity provider on OIDC enabled k8s #20362Additional context
The text was updated successfully, but these errors were encountered: