| layout | title | categories | tags | status | type | published | meta |
|---|---|---|---|---|---|---|---|
page |
Privacy |
publish |
page |
true |
I work on privacy research projects for the iOS platform in my free time. Those projects are in no way affiliated with my work or my employer.
My privacy research posts and tweets had more than 25,000,000 impressions. The goal is to raise awareness of what technology can do, and educate on how you, as a user, can protect yourself.
If you write a story about any of those posts, make sure to read the original blog post linked, and feel free to use any of the images and videos provided on krausefx.com, as long as you reference the original blog post, including my name.
If you need any additional resources, or have any follow-up questions that are not covered by the blog post, feel free to reach out to me directly, either on Twitter or via email.
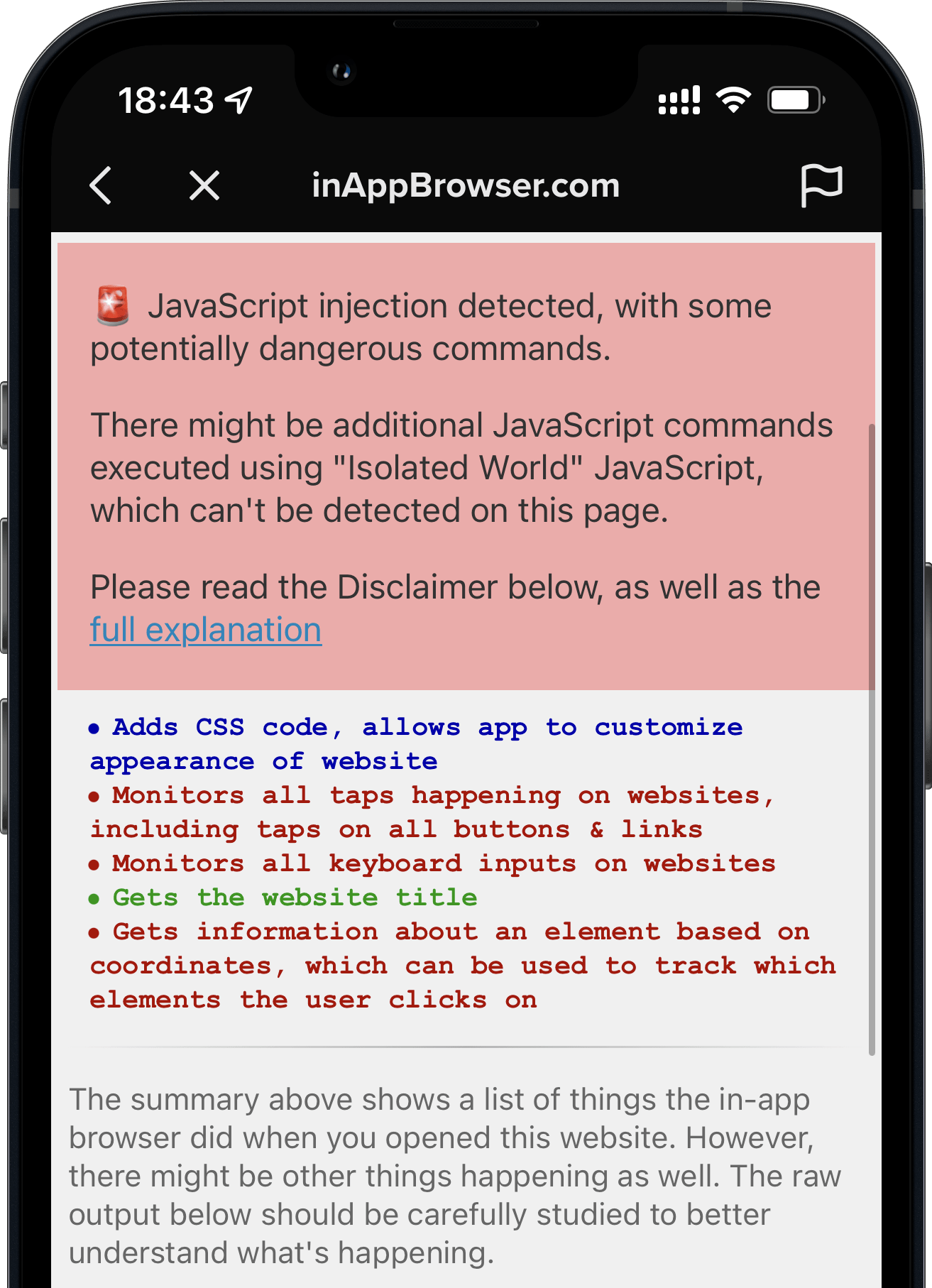
- Introducing InAppBrowser.com, an open source website to see the JavaScript commands that get injected through in-app browsers
- When opening a website from within the TikTok iOS app, they inject code that can observe every keyboard input (which may include credit card details, passwords or other sensitive information)
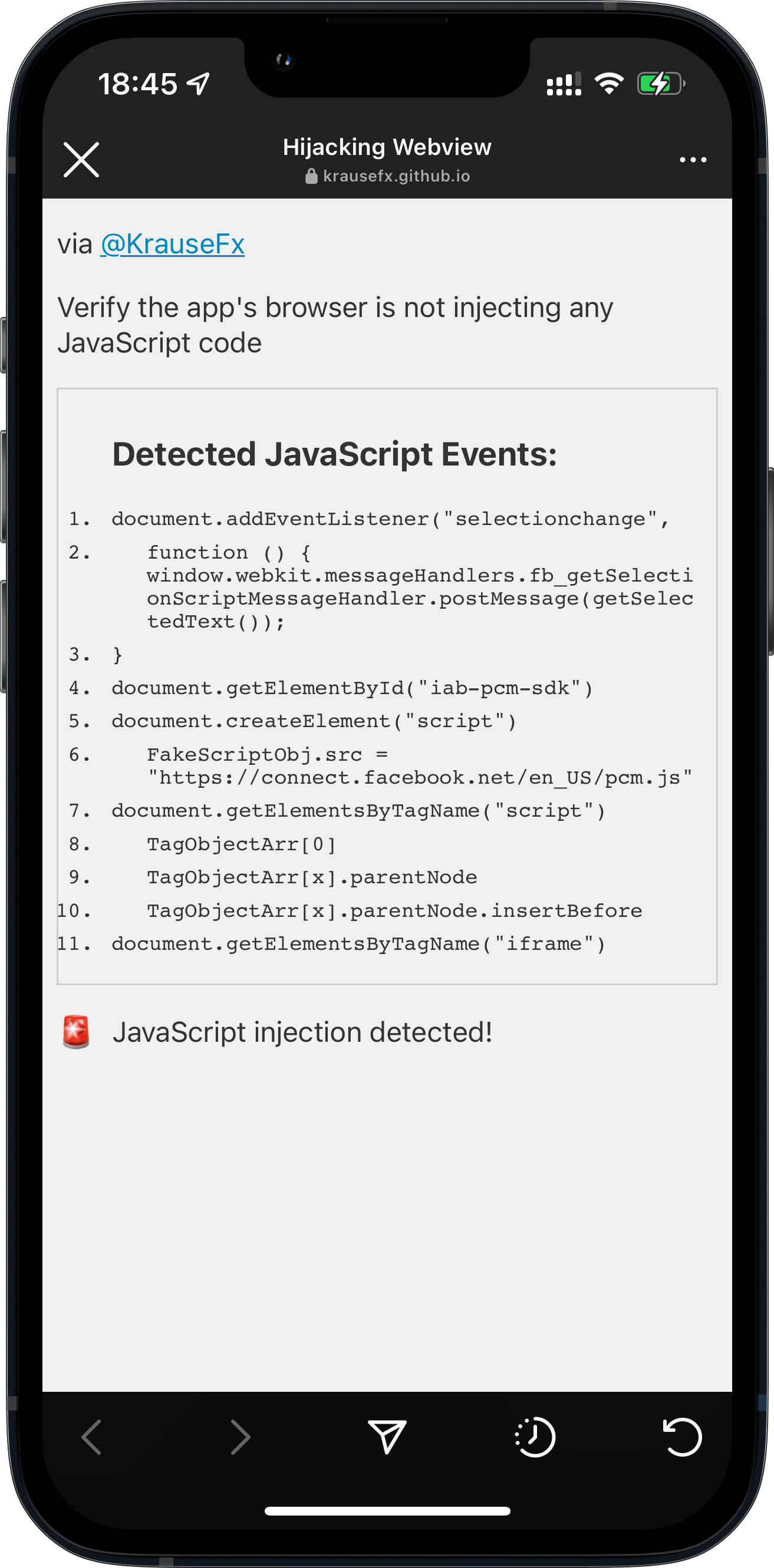
- How Instagram for iOS also injects JavaScript code to observe all taps happening inside their in-app browser, like clicking on buttons, links or images.
- How as of iOS 14.3, apps can easily hide their JavaScript activities from websites using WKContentWorld.
The iOS Instagram and Facebook app render all third party links and ads within their app using a custom in-app browser. This causes various risks for the user, with the host app being able to track every single interaction with external websites, from all form inputs like passwords and addresses, to every single tap.
- Links to external websites are rendered inside the Instagram app, instead of using the built-in Safari.
- This allows Instagram to monitor everything happening on external websites, without the consent from the user, nor the website provider.
- The Instagram app injects their JavaScript code into every website shown, including when clicking on ads. Even though the injected script doesn't currently do this, running custom scripts on third party websites allows them to monitor all user interactions, like every button & link tapped, text selections, screenshots, as well as any form inputs, like passwords, addresses and credit card numbers.
Do you want the user’s Apple ID password, to get access to their Apple account, or to try the same email/password combination on different web services? Just ask your users politely, they’ll probably just hand over their credentials, as they’re trained to do so 👌
One of these is Apple asking you for your password and the other one is a phishing popup that steals your password.
How can you protect yourself? Press the home button and open the iCloud settings manually
Every iOS app you ever gave permission to use your camera can record you any time it runs - without notice
Once you grant an app access to your camera, it can
- access both the front and the back camera
- record you at any time the app is in the foreground
- take pictures and videos without telling you
- upload the pictures/videos it takes immediately
- run real-time face recognition to detect facial features or expressions
- Have you ever used a social media app while using the bathroom? 🚽
All without indicating that your phone is recording you and your surrounding, no LEDs, no light or any other kind of indication.
## [detect.location](/blog/ios-privacy-detectlocation-an-easy-way-to-access-the-users-ios-location-data-without-actually-having-access)
Once the user grants access to the image library (e.g. to upload a single photo as a profile picture), an iOS app can
- Get a history of the cities, countries, and other places a user has visited, as long as they took a picture there
- Find the user's place of work, by figuring out where they are from 9 to 5
- Get a complete list of the user's cameras and photography devices (which iPhones, Android phones, cameras) and how long they used each device
- Use facial recognization to find out who the user hangs out with and who their partner is. Is the user single?
- Understand the user's background:
- Did the user attend college? If so, which one?
- Did the user recently move from the suburbs to the city?
- Does the user spend a lot of time with their family?
Sandboxed Mac apps can record your entire screen at any time, without you knowing.
Running the screen through simple OCR software, this allows the attacker to access personal information, like emails, messages, API keys and more
- Take screenshots of your Mac silently without you knowning
- Access every pixel, even if the Mac app is in the background
- Use basic OCR software to read the text on the screen
- Access all connected monitors
What's the worst that could happen?
- Read password and keys from password managers
- Detect what web services you use (e.g. email provider)
- Read all emails and messages you open on your Mac
- When a developer is targeted, this allows the attacker to potentially access sensitive source code, API keys or similar data
- Learn personal information about the user, like their bank details, salary, address, etc.
Third-party SDKs can often easily be modified while you download them! Using a simple person-in-the-middle attack, anyone in the same network can insert malicious code into the SDK, and with that into your application, as a result running in your user's pockets. A person-in-the-middle attack in this context works by interfering network traffic and insert malicious code into the SDK.
31% of the most popular closed-source iOS SDKs are vulnerable to this attack, as well as a total of 623 CocoaPods. As part of this research I notified the affected parties, and submitted patches to CocoaPods to warn developers and SDK providers.
Mobile Safari notifies the server as soon as the user hits the Share button, telling the website operator that this content will likely be shared somewhere else.
Custom in-app browsers in iOS apps have full access to the web content, including any JavaScript variables, the full HTML DOM and more. This allows apps to steal the user's sessions, passwords, keys and more.
Any website you're visiting instantly gets access to your smartphone's acceleration and gyro sensor values in real-time without asking the user for permission.
As a result, any website you visit, can do a pretty precise guess on if you are:
- sitting
- standing
- walking
- running
- driving
- taking a picture
- taking a selfie
- lying in bed, laying the phone on a table