A security oriented, feedback-driven, evolutionary, easy-to-use fuzzer with interesting analysis options. See USAGE for the description of command-line options.
- It's multi-process and multi-threaded: no need to run multiple copies of your fuzzer, as honggfuzz can unlock potential of all your available CPU cores with a single supervising process. The file corpus is automatically shared and improved between the fuzzing threads and fuzzed processes.
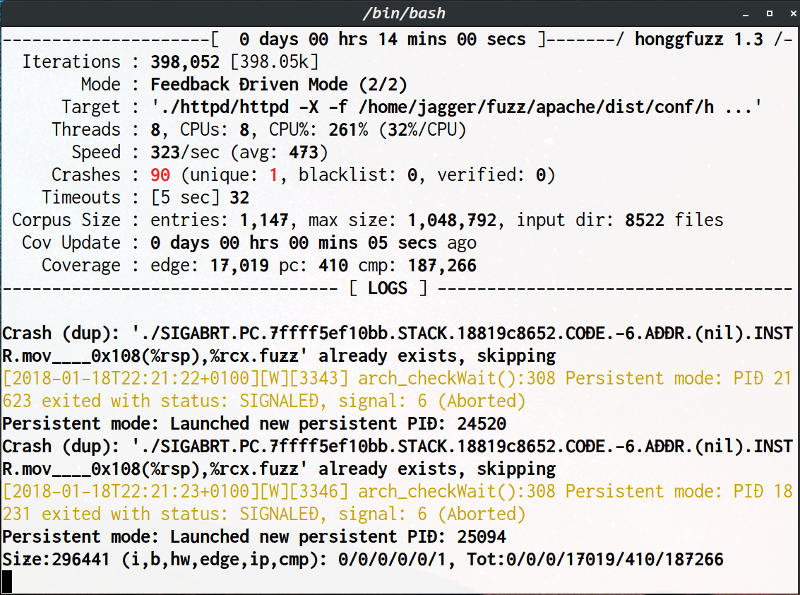
- It's blazingly fast when in the persistent fuzzing mode). A simple/empty LLVMFuzzerTestOneInput function can be tested with up to 1mo iterations per second on a relatively modern CPU (e.g. i7-6700K)
- Has a solid track record of uncovered security bugs: the only (to the date) vulnerability in OpenSSL with the critical score mark was discovered by honggfuzz. See the Trophies paragraph for the summary of findings to the date
- Uses low-level interfaces to monitor processes (e.g. ptrace under Linux and NetBSD). As opposed to other fuzzers, it will discover and report hijacked/ignored signals from crashes (intercepted and potentially hidden by a fuzzed program)
- Easy-to-use, feed it a simple corpus directory (can even be empty) and it will work its way up expanding it utilizing feedback-based coverage metrics
- Supports several (more than any other coverage-based feedback-driven fuzzer) hardware-based (CPU: branch/instruction counting, Intel BTS, Intel PT) and software-based feedback-driven fuzzing methods known from other fuzzers (libfuzzer, afl)
- Works (at least) under GNU/Linux, FreeBSD, NetBSD, Mac OS X, Windows/CygWin and Android
- Supports the persistent fuzzing mode (long-lived process calling a fuzzed API repeatedly) with libhfuzz/libhfuzz.a. More on that can be found here
- It comes with the examples directory, consisting of real world fuzz setups for widely-used software (e.g. Apache and OpenSSL)
- Linux - The BFD library (libbfd-dev) and libunwind (libunwind-dev/libunwind8-dev), clang-4.0 or higher for software-based coverage modes
- FreeBSD - gmake, clang-3.6 or newer (clang-devel/4.0 suggested)
- NetBSD - gmake, clang, capstone, libBlocksRuntime
- Android - Android SDK/NDK. Also see this detailed doc on how to build and run it
- Windows - CygWin
- Darwin/OS X - Xcode 10.8+
- if Clang/LLVM is used to compile honggfuzz - link it with the BlocksRuntime Library (libblocksruntime-dev)
Honggfuzz has been used to find a few interesting security problems in major software packages; An incomplete list:
- Pre-auth remote crash in OpenSSH
- Apache HTTPD
- Various SSL libs
- Remote OOB read in OpenSSL • CVE-2015-1789
- Remote Use-after-Free (potential RCE, rated as critical) in OpenSSL • CVE-2016-6309
- Remote OOB write in OpenSSL • CVE-2016-7054
- Remote OOB read in OpenSSL • CVE-2017-3731
- Uninitialized mem use in OpenSSL
- Crash in LibreSSL
- Invalid free in LibreSSL
- Uninitialized mem use in BoringSSL
- Adobe Flash memory corruption • CVE-2015-0316
- Multiple bugs in the libtiff library
- Multiple bugs in the librsvg library
- Multiple bugs in the poppler library
- Multiple exploitable bugs in IDA-Pro
- Remote DoS in Crypto++ • CVE-2016-9939
- Programming language interpreters
- Double-free in LibXMP
- Heap buffer overflow in SAPCAR • CVE-2017-8852
- Crashes in libbass
- FreeType 2:
- Infinite loop in NGINX Unit
- A couple of problems in the MATLAB MAT File I/O Library: #1, #2, #3, #4, #5
- Samba's tdbdump + tdbtool
- Crash in djvulibre
- Rust:
- ... and more
- QuickFuzz by CIFASIS
- OSS-Fuzz
- Frog And Fuzz
- dyjakan's interpreters fuzzing project
- riufuzz: honggfuzz with AFL-like UI
- h2fuzz: fuzzing Apache's HTTP/2 implementation
- honggfuzz-dharma: honggfuzz with dharma grammar fuzzer
- Owl: a system for finding concurrency attacks
- honggfuzz-docker-apps
- FFW - Fuzzing For Worms
- honggfuzz-rs: fuzzing Rust with Honggfuzz
- roughenough-fuzz
- Rust's fuzztest
- Monkey: a HTTP server
- Killerbeez API
- FuzzM: a gray box model-based fuzzing framework
- FuzzOS: by Mozilla Security
- Android: by OHA
- QDBI: by Quarkslab
The examples directory contains code demonstrating (among others) how to use honggfuzz to find bugs in the OpenSSL library and in the Apache HTTPD web server.
- User mailing list: honggfuzz@googlegroups.com, sign up with this link.
This is NOT an official Google product