-
Notifications
You must be signed in to change notification settings - Fork 0
Metasploit support
Kvasir's support for Metasploit can vary based upon the variation installed.
The free Metasploit Framework has the most limited support. Only the ability to process the credentials CSV output is provided. Additional support for the Metasploit Data Module (MDM) will be incorporated after Rapid7 implements its latest changes.
For those using the Metasploit Framework and want to import account data, from msfconsole perform the following:
msf> creds (options) -o output.csv
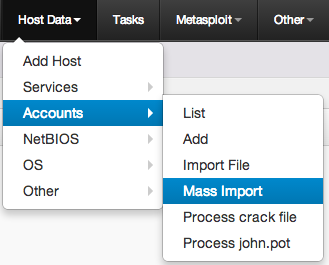
Import the results through the Host Data -> Accounts -> Mass Import menu selection:
The primary Metasploit Pro settings are configured in each user's profile. This allows each user to have their own Metasploit Pro instance.
Profile setting values:
- Metasploit Pro API Key: Key to communicate to the Metasploit API
- Metasploit Pro URL: URL to communicate to Metasploit Pro (default: https://localhost:3790/)
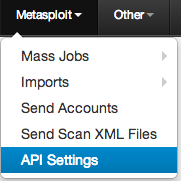
Alternatively these can be set from the Metasploit -> API Settings menu selection.
Setting values:
- Workspace Name: With a valid API Key/URL a list of Workspaces will be listed for selection
- Workspace Number: The numerical entry of the Workspace is required so Kvasir can provide links to Metasploit Pro for certain results. This number can be found by looking at your Metasploit URL. For example the workspace number is 10 for the URL https://localhost:3790/workspaces/10.
- MSF User: The user to assign any imported hosts to
- Metasploit Pro API Key: Key to communicate to the Metasploit API
- Metasploit Pro URL: URL to communicate to Metasploit Pro (default: https://localhost:3790/)
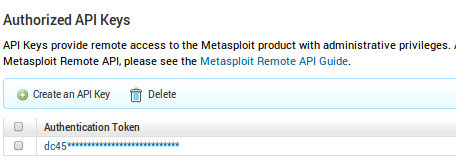
The Metasploit Pro API Key is created in Metasploit Pro's Administration -> Global Settings:
There are two "Mass job" functions provided by Metasploit Pro, "Bruteforce" and "Exploit". Each one acts upon a list of IP Addresses. These addresses must already exist within Metasploit Pro - it will not add them to its own database.
Due to the limited Metasploit Pro API Kvasir only supports importing Report XML, PWDUMP and Screenshot data. Other formats will be added when Rapid7 releases an updated API.
Metasploit XML Reports must be manually generated in Metasploit Pro from the Reports -> Export Data menu. Only "XML Export" is required.
Options:
- Metasploit XML File: XML File to Import
- Engineer: Engineer to assign hosts to
- Asset Group: Asset group to assign hosts to
- Hosts to Only Include: A list of IP Addresses that will be imported, all non-matching will be skipped
- Hosts to Ignore: A blacklist of IP Addresses to skip during importing
- Update Existing Hosts: Update existing hosts, otherwise skip them
- Run in background task: Send to the scheduler to run in the background
It is possible to send account information from Kvasir to Metasploit Pro. Accounts are not overwritten in Metasploit Pro so duplicates are possible. Most Metasploit bruteforce scripts cull duplicates before sending login requests.
Scan result data stored in $KVASIR/data/scanfiles can be passed to Metasploit Pro for parsing/entry.