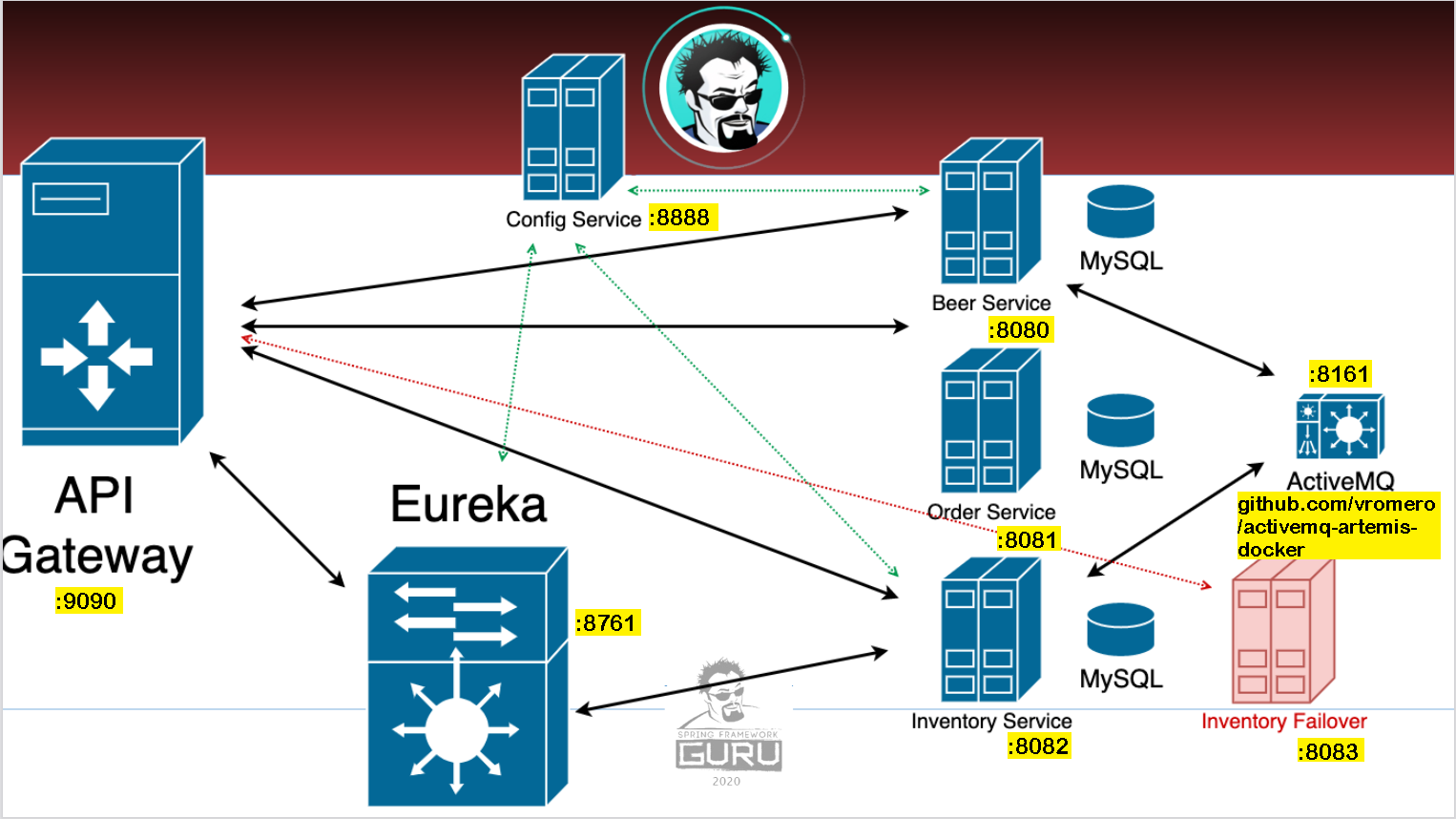
| Project | |
|---|---|
| KWG MICROSERVICES BREWERY | |
| Service Name | Port |
| Brewery Beer Service | 8080 |
| Brewery Beer Order Service | 8081 |
| Brewery Beer Inventory Service | 8082 |
| Inventory Failover Service | 8083 |
| Netflix Eureka Server | 8761 |
| Spring Cloud Gateway Server | 9090 |
| Spring Cloud Config Server | 8888 |
| Brewery Cloud Config Repo | ----- |
-
-
Setting up a single application using Spring Cloud Configuration
- Create directories for each of the Spring Boot Microservices
- Add configurations for active profiles
- Goal - setup application with profile configuration and test in Postman
-
Spring Cloud Config RESTful Endpoints
-
.Configuration Endpoints available endpoints:
- /{application}/{profile}[/{label}]
- /{appliucation}-{profile}.yml
- /{label}/{application}-{profile}.yml
- /{application}-{profile}.properties -/{label}/{application}-{profile}.properties
-
if you do /{application} you will get 404 Not Found
-
if you do /{application}/default you will get properties
-
John notes he has never had a use for labels in configuration
- Suggests, if you need it, question why you need it
-
-
-
Spring Cloud Security
-
Property Encryption / Decryption
- At Rest Encryption with Spring CLoud Config
- Spring Cloud Configuration supports property encryption and decryption
- Should be used for sensitive data and passwords
- Java Cryptography Extension (JCE)
- Prior to Java 8 u162 required additional setup
- Older examples will refer to download and install JCE
- Included by default in Java 11+
- At Rest Encryption with Spring CLoud Config
-
Configuration
- Spring Cloud Configuration will store encrypted properties as:
- {cyper}
- When a Spring Cloud Config client requests an encrypted property the value is decrypted and presented to the client in the request
- Must set a symmetric key in property 'encrypt.key' - should prefer setting this as an environment variable
- Asymmetric (public / private) keys also supported - see docs for details
- Spring Cloud Configuration will store encrypted properties as:
-
Encryption / Decryption
- Spring CLoud Configuration provides endpoints for property encryption / decryption
- POST /encrypt - will encrypt body of post
- POST /decrypt - will decrypt body of post
- Spring CLoud Configuration provides endpoints for property encryption / decryption
-
Security Retrospective
-
Problems with HTTP Basic Autentication
- Eureka Clients sending id / passwords plain text
- Other clients send in header with base64 encoding
- Easily converted to plain text
- Sent in each request - thus more exposure to attack
- HTTPS can be used to mitigate security riks with HTTP Basic
-
Problems with using User ID / Password
- Sending password to multiple servers
- Validation overhead
- ie, need to verify credentials with authentication server, which becomes a scalability bottleneck
- Mitigation - Use tokens such as JWT which can be trusted and authenticated by each service
-
Encryption in Flight
- HTTPS for RESTful services
- Should be a 'must' for public networks
- Should be highly considered for internal networks
- There is a CPU cost to using HTTPS - but less of concern than in the past
- Use encrypted connections for network communication to databases and message brokers (ActiveMQ - JMS, etc.)
- Typically is not, options vary per implementation
- HTTPS for RESTful services
-
Encryption at rest:
- Consider using encrypted file systems
- Databases and message brokers have encryption options for data stored
- Don't overlook backups. Backup files should also be encrypted
-