- Website https://keel.sh
- Slack - kubernetes.slack.com look for channel #keel
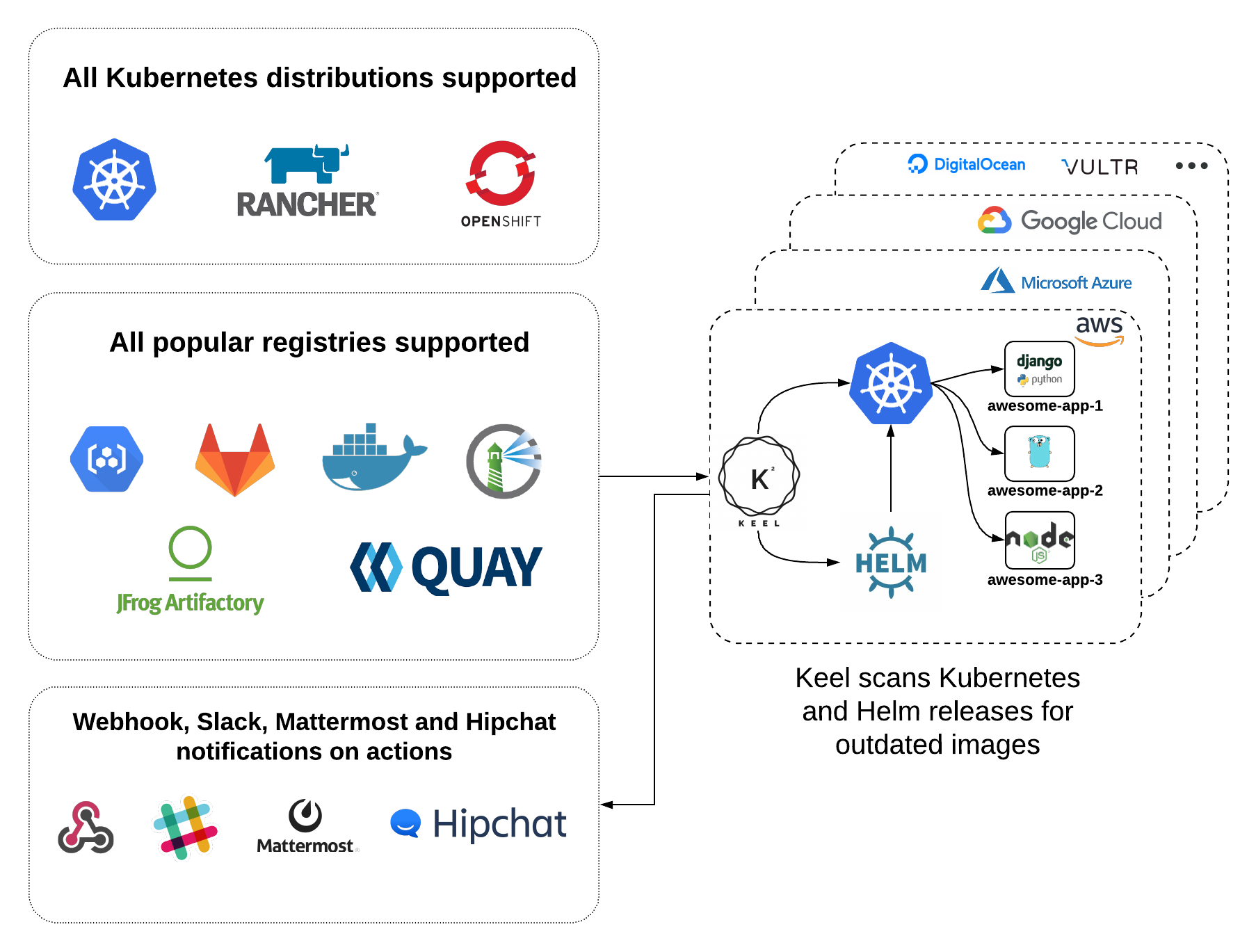
Keel is a tool for automating Kubernetes deployment updates. Keel is stateless, robust and lightweight.
Keel provides several key features:
-
Kubernetes and Helm providers - Keel has direct integrations with Kubernetes and Helm.
-
No CLI/API - tired of
f***ctlfor everything? Keel doesn't have one. Gets job done through labels, annotations, charts. -
Semver policies - specify update policy for each deployment/Helm release individually.
-
Automatic Google Container Registry configuration - Keel automatically sets up topic and subscriptions for your deployment images by periodically scanning your environment.
-
Native, DockerHub, Quay and Azure container registry webhooks support - once webhook is received impacted deployments will be identified and updated.
-
Polling - when webhooks and pubsub aren't available - Keel can still be useful by checking Docker Registry for new tags (if current tag is semver) or same tag SHA digest change (ie:
latest). -
Notifications - out of the box Keel has Slack, Hipchat, Mattermost and standard webhook notifications, more info here
Support Keel's development by:
- Star this repository
- Follow on Twitter
Prerequisites:
- Helm
- Kubernetes
You need to add this Chart repo to Helm:
helm repo add keel https://keel-hq.github.io/keel/
helm repo updateInstall through Helm (with Helm provider enabled by default):
helm upgrade --install keel --namespace=kube-system keel/keelIf you work mostly with regular Kubernetes manifests, you can install Keel without Helm provider support:
helm upgrade --install keel --namespace=keel keel/keel --set helmProvider.enabled="false" To install for Helm v3, set helmProvider.version="v3" (default is "v2"):
helm install keel keel/keel --set helmProvider.version="v3" To install using terraform:
resource "helm_release" "keel" {
provider = helm.helm
name = "keel"
namespace = "keel"
repository = "https://keel-hq.github.io/keel"
chart = "keel"
version = "v1.0.4"
set {
name = "basicauth.enabled"
value = "true"
}
set {
name = "basicauth.user"
value = "admin"
}
set {
name = "basicauth.password"
value = "admin"
}
set {
name = "image.repository"
value = "keelhq/keel"
}
set {
name = "image.tag"
value = "0.19.1"
}
}That's it, see Configuration section now.
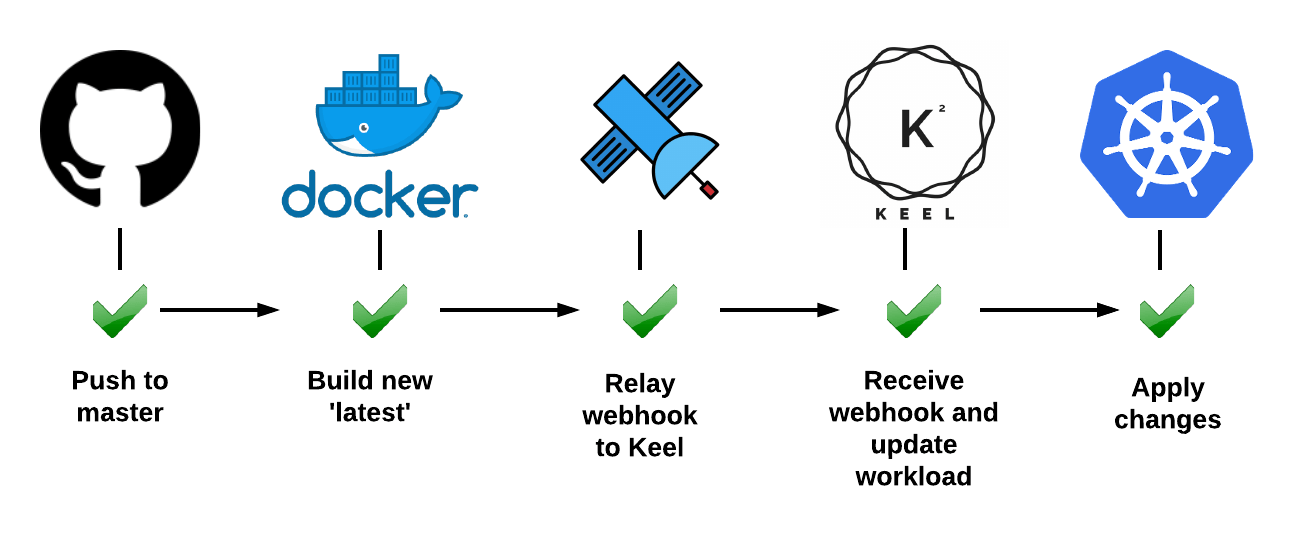
A step-by-step guide to install Keel on your Kubernetes cluster is viewable on the Keel website:
https://keel.sh/examples/#example-1-push-to-deploy
Once Keel is deployed, you only need to specify update policy on your deployment file or Helm chart:
apiVersion: apps/v1
kind: Deployment
metadata:
name: wd
namespace: default
labels:
name: "wd"
annotations:
keel.sh/policy: minor # <-- policy name according to https://semver.org/
keel.sh/trigger: poll # <-- actively query registry, otherwise defaults to webhooks
spec:
template:
metadata:
name: wd
labels:
app: wd
spec:
containers:
- image: karolisr/webhook-demo:0.0.8
imagePullPolicy: Always
name: wd
command: ["/bin/webhook-demo"]
ports:
- containerPort: 8090No additional configuration is required. Enabling continuous delivery for your workloads has never been this easy!
Documentation is viewable on the Keel Website:
https://keel.sh/docs/#introduction
Before starting to work on some big or medium features - raise an issue here so we can coordinate our efforts.
We use pull requests, so:
- Fork this repository
- Create a branch on your local copy with a sensible name
- Push to your fork and open a pull request
If you wish to work on Keel itself, you will need Go 1.12+ installed. Make sure you put Keel into correct Gopath and go build (dependency management is done through dep).
To test Keel while developing:
- Launch a Kubernetes cluster like Minikube or Docker for Mac with Kubernetes.
- Change config to use it:
kubectl config use-context docker-for-desktop - Build Keel from
cmd/keeldirectory. - Start Keel with:
keel --no-incluster. This will use Kubeconfig from your home.
# Ensure we have gcc and go
choco upgrade mingw -y
choco upgrade golang -y
# Move and build
cd cmd/keel
go build
$Env:XDG_DATA_HOME = $Env:APPDATA; # Data volume for the local database
$Env:HOME = $Env:USERPROFILE; # This is where the .kube/config will be read from
$Env:KUBERNETES_CONTEXT = "mycontext" #Use if you have more than one context in .kube/config
.\keel --no-inclusterGet a test parser (makes output nice):
go get github.com/mfridman/tparseTo run unit tests:
make testPrerequisites:
- configured kubectl + kubeconfig
- a running cluster (test suite will create testing namespaces and delete them after tests)
- Go environment (will compile Keel before running)
Once prerequisites are ready:
make e2eThe repository contains a debug version of keel container ready for remote debugging.
You can start the debug container with powershell (docker desktop needed):
.\build.ps1 -StartDebugContainersTo connect to your cluster, copy the authentication details from within the keel pod in your cluster from:
/var/run/secrets/kubernetes.io/serviceaccount
to the serviceaccount folder at the root of the repository and make sure you set the environment variable for the K8S management API endpoint:
# This can be configured in envesttings.ps1 to be picked up automatically by the build script
$ENV:KUBERNETES_SERVICE_HOST = "mycluster-o5ff3caf.hcp.myregion.azmk8s.io"
$ENV:KUBERNETES_SERVICE_PORT = "443"And make sure your API server is accesible from your client (VPN, IP whitelisting or whatever you use to secure your cluster management API).
Once started, simply use the debug option in a Go debugger, such as Jetbrains GoLand:
Debugging a Go application inside a Docker container | The GoLand Blog