-
Notifications
You must be signed in to change notification settings - Fork 57
ADFS user credentials authentication
node-sp-auth automatically determines if your organization is using federated identity and requests authentication using your ADFS server. All you need is to pass username and password, like you normally do for User Credentials. username will be equal to your's company user name, i.e. johnsmith@contoso.com.
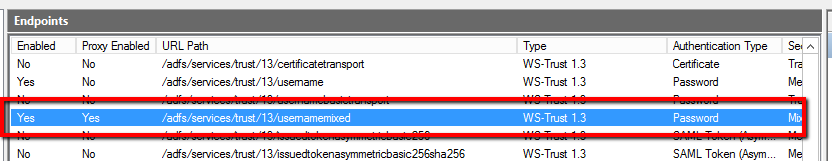
ADFS authentication uses adfs's usernamemixed endpoint (version 1.3) which is available in ADFS 2.0+ and enabled by default. In case if you have troubles authenticating with adfs, check if under adfs server this particular endpoint is enabled - AD FS -> Service -> Endpoints:
-
username- required string, your domain user name. Username can be provided in two forms: with domain and without domain. For example for userjohnsmith@contoso-corp.comyou need to providejohnsmith@contoso-corp.comasusernameoption OR{username: 'johnsmith', domain: 'contoso', password: 'pass'}. -
password- required string, password -
domain- optional string, used when you are using short username form. The easiest way to know your current domain when you are inside corporation is to runecho %USERDOMAIN%in command line -
relyingParty- required string, this parameter may vary depending on your configuration. Relying party name you setup when configuring ADFS. For on-premise you can get the name of the relying party by runningGet-SPTrustedIdentityTokenIssuercmdlet. You may have many trusted token issuers in your farm, you need to find the one responsible for ADFS authentication and copyDefaultProviderRealmparam: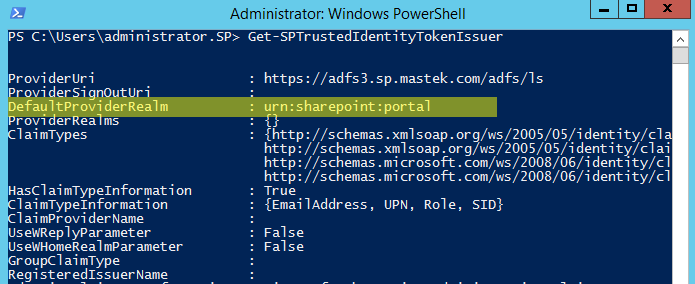
-
adfsUrl- required string, url to your adfs server -
adfsCookie- optional string, adfs cookie name. In most cases you can skip this parameter and default "FedAuth" will be used. But some organizations use custom cookie names for their ADFS configuration. In that case you can specify this custom cookie name, i.e.adfsCookie: 'FedAuth01'
{
username: 'johnsmith@contoso-corp.com',
password: 'sd46$fFF$',
relyingParty: 'urn:sharepoint:portal',
adfsUrl: 'https://adfs3'
}OR
{
username: 'johnsmith',
domain: 'contoso',
password: 'sd46$fFF$',
relyingParty: 'urn:sharepoint:portal',
adfsUrl: 'https://adfs3'
}{
headers: {
'Cookie': '<FedAuth authentication cookie>'
}
}You need to have ADFS configured and working, usernamemixed endpoint (version 1.3) enabled on ADFS server.
Also make sure that on your SharePoint web application root site collection is created.
import * as spauth from 'node-sp-auth';
import * as request from 'request-promise';
spauth
.getAuth('https://sp2013dev/sites/dev', {
username: 'johnsmith@contoso-corp.com',
password: '[password]',
relyingParty: 'urn:sharepoint:portal',
adfsUrl: 'https://adfs3'
})
.then(data => {
let headers = data.headers;
headers['Accept'] = 'application/json;odata=verbose';
request.get({
url: 'https://sp2013dev/sites/dev/_api/web',
headers: headers,
json: true
}).then(response => {
console.log(response.d.Title);
});
});- SharePoint Online
- SharePoint on-premise (2013, 2016, 2019)
- ADFS user credentials
- On demand authentication