-
Notifications
You must be signed in to change notification settings - Fork 5.9k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
OidcIdTokenValidator ensures clockSkew is positive number #6443
Comments
|
Hey @jgrandja From my initial analysis, it seems like I need to update within
Please let me know if I'm missing something. Also, was curious as to why this validation is being changed? to avoid negative EDIT: Forgot to insert validation inside Assert.isTrue 😅 |
|
@vishalvrv9 Thanks for the offer! This is yours. Yes, you have it right as far as what changes are required. The main reason for this change is to prevent the user from configuring a negative value. Also, please ensure you write a test for this. Thanks so much! |
|
Hey @jgrandja, Firstly, I tried looking for a test case within Another thing I noticed is Then, I went through this to understand the function of the clockSkew. I now understand the purpose of a clockSkew better, but from a test case perspective; still no luck. Could you help me move forward and let me know what I'm missing here? |
You're right and this test needs to be there. Looks like it was missed. Thanks for pointing that out. Can you please add this test as well. For an example of how to write this test take a look at For the negative As an FYI, our test names follow this naming convention: Does this help? |
|
Hi @vishalvrv9. How are things going? |
|
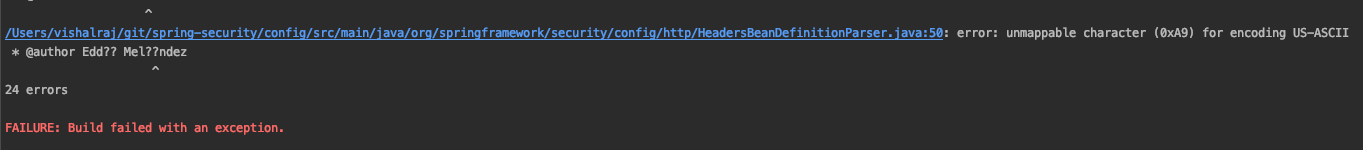
Hey @jgrandja, About the issue, I have made the necessary changes. The junit tests are passing. It seems like an encoding error because of the author's name Eddú Meléndez. Could you help me mitigate this? Update: Just went through the contributing guidelines again and changed the encoding to Latin-1 (ISO-8859-1) for the entire project. The error is still persisting. |
|
@vishalvrv9 Are you using the native Terminal application packaged with Mac OSX? You might want to look at this article. Also, I use iTerm2 for my CLI and would highly recommend this over Terminal. I've never had any encoding issues with iTerm2. See if the same problem persists using iTerm2 and let me know. Also, use this command to do a full build -> |
|
Hey @jgrandja New impediment:
Note: I've signed the contributor license agreement. Also, apologies for being sloppy and an untimely delivery. Will be extra careful in the future. 😞 |
You need to fork spring-security and than clone your fork locally. Than you will push your local branch to your fork. From your fork, you'll be able to create a PR from the branch. Makes sense? |
OidcIdTokenValidator.setClockSkew()should assert that theclockSkewis>= 0.The text was updated successfully, but these errors were encountered: