-
-
Notifications
You must be signed in to change notification settings - Fork 1k
IPC lol US
ASF INCLUDEZ ITZ OWN UNIQUE IPC INTERFACE DAT CAN BE USD 4 FURTHR INTERACSHUN WIF TEH PROCES. IPC STANDZ 4 INTR-PROCES COMMUNICASHUN AN IN DA MOST SIMPLE DEFINISHUN DIS AR TEH "ASF WEB INTERFACE" BASD ON KESTREL HTTP SERVR DAT CAN BE USD 4 FURTHR INTEGRASHUN WIF TEH PROCES, BOTH AS FRONTEND 4 END-USR (ASF-UI), AN BAKEND 4 THIRD-PARTY INTEGRASHUNS (ASF API).
IPC CAN BE USD 4 LOT OV DIFFERENT THINGS, DEPENDIN ON UR NEEDZ AN SKILLS. 4 EXAMPLE, U CAN USE IT 4 FETCHIN STATUS OV ASF AN ALL BOTS, SENDIN ASF COMMANDZ, FETCHIN AN EDITIN GLOBAL/BOT CONFIGS, ADDIN NEW BOTS, DELETIN EXISTIN BOTS, SUBMITTIN KEYS 4 BGR OR ACCESIN ASFS LOG FILE. ALL OV DOSE ACSHUNS R EXPOSD BY R API, WHICH MEANZ DAT U CAN CODE UR OWN TOOLS AN SCRIPTS DAT WILL BE ABLE 2 SPEEK WIF ASF AN INFLUENCE IT DURIN RUNTIME. IN ADDISHUN 2 DAT, SELECTD ACSHUNS (SUCH AS SENDIN COMMANDZ) R ALSO IMPLEMENTD BY R ASF-UI WHICH ALLOWS U 2 EASILY ACCES THEM THRU FRIENDLY WEB INTERFACE.
UNLES U MANUALLY DISABLD IPC THRU IPC GLOBAL CONFIGURASHUN PROPERTY, IZ ENABLD BY DEFAULT. ASF WILL STATE IPC LAUNCH IN ITZ LOG, WHICH U CAN USE 4 VERIFYIN IF IPC INTERFACE HAS STARTD PROPERLY:
INFO|ASF|Start() STARTIN IPC SERVR...
INFO|ASF|Start() IPC SERVR READY!
ASFS HTTP SERVR IZ NAO LISTENIN ON SELECTD ENDPOINTS. IF U DIDNT PROVIDE CUSTOM CONFIGURASHUN FILE 4 IPC, DOSE WILL BE IPV4-BASD 127.0.0.1 AN IPV6-BASD [::1] ON DEFAULT 1242 PORT. U CAN ACCES R IPC INTERFACE BY ABOOV LINKZ, FRUM TEH SAME MACHINE AS TEH WAN RUNNIN ASF PROCES.
ASFS IPC INTERFACE EXPOSEZ 3 DIFFERENT WAYS 2 ACCES IT, DEPENDIN ON UR PLANND USAGE.
ON TEH LOWEST LEVEL THAR IZ ASF API DAT IZ TEH CORE OV R IPC INTERFACE AN ALLOWS EVRYTHIN ELSE 2 OPERATE. DIS AR TEH WUT U WANTS 2 USE IN UR OWN TOOLS, UTILITIEZ AN PROJECTS IN ORDR 2 SPEEK WIF ASF DIRECTLY.
ON TEH MEDIUM GROUND THAR IZ R SWAGGR DOCUMENTASHUN WHICH ACTS AS FRONTEND 2 ASF API. IT FEATUREZ COMPLETE DOCUMENTASHUN OV ASF API AN ALSO ALLOWS U 2 ACCES IT MOAR EASILY. DIS AR TEH WUT U WANTS 2 CHECK IF URE PLANNIN ON WRITIN TOOL, UTILITY OR OTHR PROJECTS DAT R SUPPOSD 2 SPEEK WIF ASF THRU ITZ API.
ON TEH HIGHEST LEVEL THAR IZ ASF-UI WHICH IZ BASD ON R ASF API AN PROVIDEZ USR-FRIENDLY WAI 2 EXECUTE VARIOUS ASF ACSHUNS. DIS AR TEH R DEFAULT IPC INTERFACE DESIGND 4 END-USERS, AN PERFIK EXAMPLE OV WUT U CAN BUILD WIF ASF API. IF UD LIEK, U CAN USE UR OWN CUSTOM WEB UI 2 USE WIF ASF, BY SPECIFYIN --path COMMAND-LINE ARGUMENT AN USIN CUSTOM www DIRECTORY LOCATD THAR.
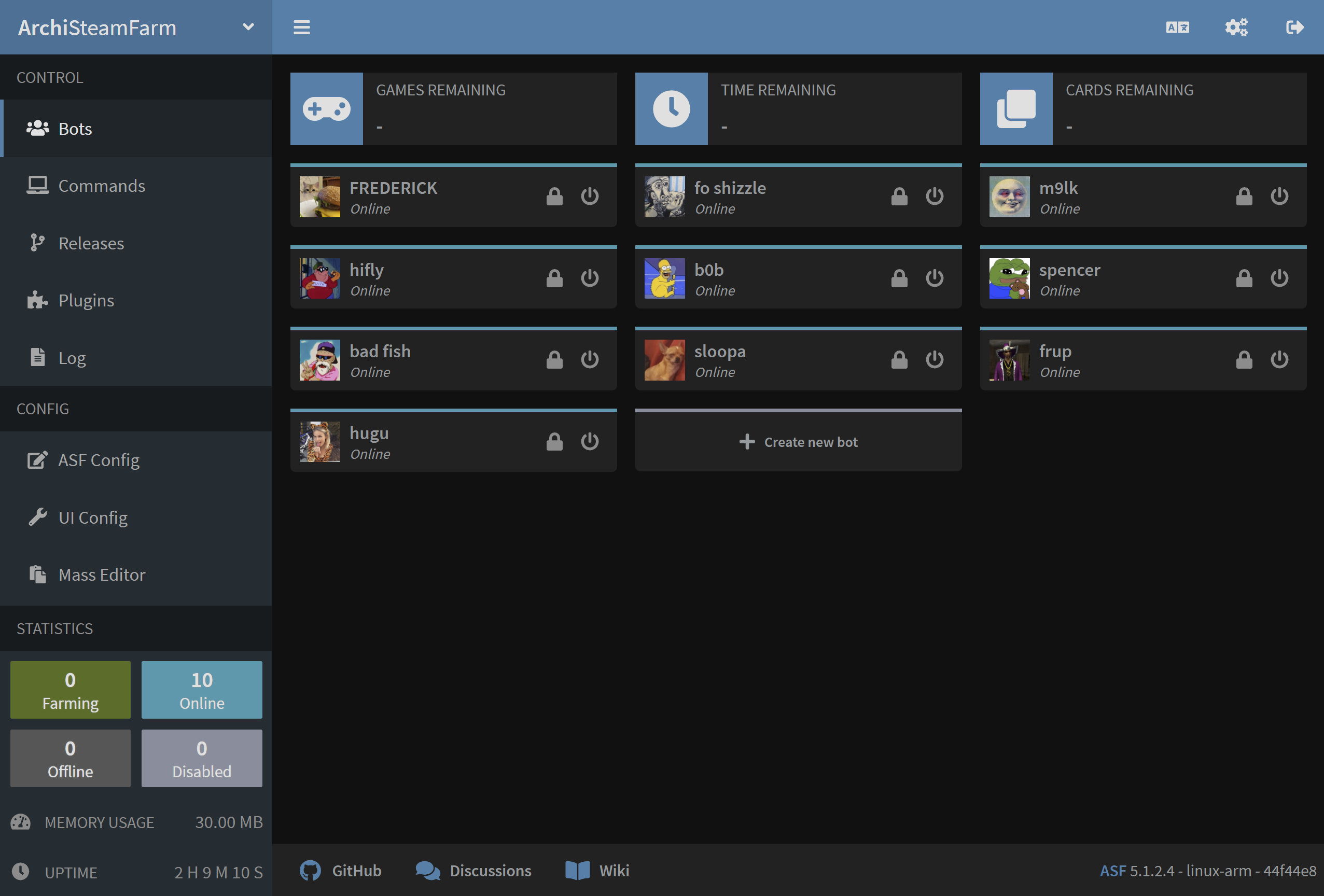
ASF-UI IZ COMMUNITY PROJECT DAT AIMS 2 CREATE USR-FRIENDLY GRAFICAL WEB INTERFACE 4 END-USERS. IN ORDR 2 ACHIEVE DAT, IT ACTS AS FRONTEND 2 R ASF API, ALLOWIN U 2 DO VARIOUS ACSHUNS WIF EASE. DIS AR TEH TEH DEFAULT UI DAT ASF COMEZ WIF.
AS STATD ABOOV, ASF-UI IZ COMMUNITY PROJECT DAT ISNT MAINTAIND BY CORE ASF DEVELOPERS. IT FOLLOWS ITZ OWN FLOW IN ASF-UI REPO WHICH SHUD BE USD 4 ALL RELATD QUESHUNS, ISSUEZ, BUG REPORTS AN SUGGESHUNS.
U CAN USE ASF-UI 4 GENERAL MANAGEMENT OV ASF PROCES. IT ALLOWS 4 EXAMPLE 2 MANAGE BOTS, MODIFY SETTINGS, SEND COMMANDZ, AN ACHIEVE SELECTD OTHR FUNCSHUNALITY NORMALLY AVAILABLE THRU ASF.
R ASF API IZ TYPICAL RESTFUL WEB API DAT IZ BASD ON JSON AS ITZ PRIMARY DATA FORMAT. WERE DOIN R BEST 2 PRECISELY DESCRIBE RESPONSE, USIN BOTH HTTP STATUS CODEZ (WER APPROPRIATE), AS WELL AS RESPONSE U CAN PARSE YOURSELF IN ORDR 2 KNOE WHETHR TEH REQUEST SUCCEEDD, AN IF NOT, DEN Y.
R ASF API CAN BE ACCESD BY SENDIN APPROPRIATE REQUESTS 2 APPROPRIATE /Api ENDPOINTS. U CAN USE DOSE API ENDPOINTS 2 MAK UR OWN HELPR SCRIPTS, TOOLS, GUIS AN ALIKE. DIS AR TEH EGSAKTLY WUT R ASF-UI ACHIEVEZ UNDR TEH HOOD, AN EVRY OTHR TOOL CAN ACHIEVE TEH SAME. ASF API IZ OFFICIALLY SUPPORTD AN MAINTAIND BY CORE ASF TEAM.
4 COMPLETE DOCUMENTASHUN OV AVAILABLE ENDPOINTS, DESCRIPSHUNS, REQUESTS, RESPONSEZ, HTTP STATUS CODEZ AN EVRYTHIN ELSE CONSIDERIN ASF API, PLZ REFR 2 R SWAGGR DOCUMENTASHUN.
R IPC INTERFACE SUPPORTS EXTRA CONFIG FILE, IPC.config DAT SHUD BE PUT IN STANDARD ASFS config DIRECTORY.
WHEN AVAILABLE, DIS FILE SPECIFIEZ ADVANCD CONFIGURASHUN OV ASFS KESTREL HTTP SERVR, TOGETHR WIF OTHR IPC-RELATD TUNIN. UNLES U HAS PARTICULAR NED, THAR IZ NO REASON 4 U 2 USE DIS FILE, AS ASF IZ ALREADY USIN SENSIBLE DEFAULTS IN DIS CASE.
TEH CONFIGURASHUN FILE IZ BASD ON FOLLOWIN JSON STRUCCHUR:
{
"Kestrel": {
"Endpoints": {
"example-http4": {
"Url": "http://127.0.0.1:1242"
},
"example-http6": {
"Url": "http://[::1]:1242"
},
"example-https4": {
"Url": "https://127.0.0.1:1242",
"Certificate": {
"Path": "/path/to/certificate.pfx",
"Password": "passwordToPfxFileAbove"
}
},
"example-https6": {
"Url": "https://[::1]:1242",
"Certificate": {
"Path": "/path/to/certificate.pfx",
"Password": "passwordToPfxFileAbove"
}
}
},
"KnownNetworks": [
"10.0.0.0/8",
"172.16.0.0/12",
"192.168.0.0/16"
],
"PathBase": "/"
}
}Endpoints - DIS AR TEH COLLECSHUN OV ENDPOINTS, EACH ENDPOINT HAVIN ITZ OWN UNIQUE NAYM (LIEK example-http4) AN Url PROPERTY DAT SPECIFIEZ Protocol://Host:Port LISTENIN ADDRES. BY DEFAULT, ASF LISTENS ON IPV4 AN IPV6 HTTP ADDRESEZ, BUT WEVE ADDD HTTPS EXAMPLEZ 4 U 2 USE, IF NEEDD. U SHUD DECLARE ONLY DOSE ENDPOINTS DAT U NED, WEVE INCLUDD 4 EXAMPLE ONEZ ABOOV SO U CAN EDIT THEM EASIR.
Host ACCEPTS EITHR localhost, FIXD IP ADDRES OV TEH INTERFACE IT SHUD LISTEN ON (IPV4/IPV6), OR * VALUE DAT BINDZ ASFS HTTP SERVR 2 ALL AVAILABLE INTERFACEZ. USIN OTHR VALUEZ LIEK mydomain.com OR 192.168.0.* ACTS TEH SAME AS *, THAR IZ NO IP FILTERIN IMPLEMENTD, THEREFORE BE EXTREMELY CAREFUL WHEN U USE Host VALUEZ DAT ALLOW REMOTE ACCES. DOIN SO WILL ENABLE ACCES 2 ASFS IPC INTERFACE FRUM OTHR MACHINEZ, WHICH CUD POSE SECURITY RISK. WE STRONGLY RECOMMEND 2 USE IPCPassword (AN PREFERABLY UR OWN FIREWALL 2) AT MINIMUM IN DIS CASE.
KnownNetworks - DIS OPSHUNAL VARIABLE SPECIFIEZ NETWORK ADDRESEZ WHICH WE CONSIDR TRUSTWORTHY. BY DEFAULT, ASF IZ CONFIGURD 2 TRUST LOOPBACK INTERFACE (localhost, SAME MACHINE) ONLY. DIS PROPERTY IZ USD IN 2 WAYS. FIRSTLY, IF U OMIT IPCPassword, DEN WELL ALLOW ONLY MACHINEZ FRUM KNOWN NETWORKZ 2 ACCES ASFS API, AN DENY EVRYBODY ELSE AS SECURITY MEASURE. SECONDLY, DIS PROPERTY IZ CRUSHUL IN REGARDZ 2 REVERSE-PROXIEZ ACCESIN ASF, AS ASF WILL HONOR ITZ HEADERS ONLY IF TEH REVERSE-PROXY SERVR IZ FRUM WITHIN KNOWN NETWORKZ. HONORIN TEH HEADERS IZ CRUSHUL IN REGARDZ 2 ASFS ANTI-BRUTEFORCE MECHANISM, AS INSTEAD OV BANNIN TEH REVERSE-PROXY IN CASE OV PROBLEM, ITLL BAN TEH IP SPECIFID BY TEH REVERSE-PROXY AS TEH SOURCE OV TEH ORIGINAL MESAGE. BE EXTREMELY CAREFUL WIF TEH NETWORKZ U SPECIFY HER, AS IT ALLOWS POTENTIAL IP SPOOFIN ATTACK AN UNAUTHORIZD ACCES IN CASE TEH TRUSTD MACHINE IZ COMPROMISD OR WRONGLY CONFIGURD.
PathBase - DIS AR TEH OPSHUNAL BASE PATH DAT WILL BE USD BY IPC INTERFACE. DEFAULTS 2 / AN SHOULDNT BE REQUIRD 2 MODIFY 4 MAJORITY OV USE CASEZ. BY CHANGIN DIS PROPERTY ULL HOST ENTIRE IPC INTERFACE ON CUSTOM PREFIX, 4 EXAMPLE http://localhost:1242/MyPrefix INSTEAD OV http://localhost:1242 ALONE. USIN CUSTOM PathBase CUD BE WANTD IN COMBINASHUN WIF SPECIFIC SETUP OV REVERSE PROXY WER UD LIEK 2 PROXY SPECIFIC URL ONLY, 4 EXAMPLE mydomain.com/ASF INSTEAD OV ENTIRE mydomain.com DOMAIN. NORMALLY DAT WUD REQUIRE FRUM U 2 RITE REWRITE RULE 4 UR WEB SERVR DAT WUD MAP mydomain.com/ASF/Api/X -> localhost:1242/Api/X, BUT INSTEAD U CAN DEFINE CUSTOM PathBase OV /ASF AN ACHIEVE EASIR SETUP OV mydomain.com/ASF/Api/X -> localhost:1242/ASF/Api/X.
UNLES U TRULY NED 2 SPECIFY CUSTOM BASE PATH, IZ BEST 2 LEEF IT AT DEFAULT.
TEH FOLLOWIN CONFIG SIMPLY CHANGEZ DEFAULT ASF LISTENIN PORT FRUM 1242 2 1337. U CAN PICK ANY PORT U LIEK, BUT WE RECOMMEND 1024-32767 RANGE, AS OTHR PORTS R TYPICALLY REGISTERD, AN CUD 4 EXAMPLE REQUIRE root ACCES ON LINUX.
{
"Kestrel": {
"Endpoints": {
"HTTP4": {
"Url": "http://127.0.0.1:1337"
},
"HTTP6": {
"Url": "http://[::1]:1337"
}
}
}
}TEH FOLLOWIN CONFIG WILL ALLOW REMOTE ACCES FRUM ALL SOURCEZ, THEREFORE U SHUD ENSURE DAT U READ AN UNDERSTOOD R SECURITY NOTICE BOUT DAT, AVAILABLE ABOOV.
{
"Kestrel": {
"Endpoints": {
"HTTP": {
"Url": "http://*:1242"
}
}
}
}IF U DO NOT REQUIRE ACCES FRUM ALL SOURCEZ, BUT 4 EXAMPLE UR LAN ONLY, DEN IZ MUTCH BETTR IDEA 2 CHECK LOCAL IP ADDRES OV TEH MACHINE HOSTIN ASF, 4 EXAMPLE 192.168.0.10 AN USE IT INSTEAD OV * IN EXAMPLE CONFIG ABOOV.
ASF IPC INTERFACE BY DEFAULT DOEZ NOT REQUIRE ANY SORT OV AUTHENTICASHUN, AS IPCPassword IZ SET 2 null. HOWEVR, IF IPCPassword IZ ENABLD BY BEAN SET 2 ANY NON-EMPTY VALUE, EVRY CALL 2 ASFS API REQUIREZ TEH PASWORD DAT MATCHEZ SET IPCPassword. IF U OMIT AUTHENTICASHUN OR INPUT WRONG PASWORD, ULL GIT 401 - Unauthorized ERROR. AFTR 5 FAILD AUTHENTICASHUN ATTEMPTS (WRONG PASWORD), ULL GIT TEMPORARILY BLOCKD WIF 403 - Forbidden ERROR.
AUTHENTICASHUN CAN BE DUN THRU 2 SEPARATE WAYS.
IN GENERAL U SHUD USE HTTP REQUEST HEADERS, BY SETTIN Authentication FIELD WIF UR PASWORD AS VALUE. TEH WAI OV DOIN DAT DEPENDZ ON TEH AKSHUL TOOL URE USIN 4 ACCESIN ASFS IPC INTERFACE, 4 EXAMPLE IF URE USIN curl DEN U SHUD ADD -H 'Authentication: MyPassword' AS PARAMETR. DIS WAI AUTHENTICASHUN IZ PASD IN DA HEADERS OV TEH REQUEST, WER IT IN FACT SHUD TAEK PLACE.
ALTERNATIVELY U CAN APPEND password PARAMETR 2 TEH END OV TEH URL URE BOUT 2 CALL, 4 EXAMPLE BY CALLIN /Api/ASF?password=MyPassword INSTEAD OV /Api/ASF ALONE. DIS APPROACH IZ GUD ENOUGH, BUT OBVIOUSLY IT EXPOSEZ PASWORD IN DA OPEN, WHICH IZ NOT NECESARILY ALWAYS APPROPRIATE. IN ADDISHUN 2 DAT IZ EXTRA ARGUMENT IN DA QUERY STRIN, WHICH COMPLICATEZ TEH LOOK OV TEH URL AN MAKEZ IT FEELZ LIEK IZ URL-SPECIFIC, WHILE PASWORD APPLIEZ 2 ENTIRE ASF API COMMUNICASHUN.
BOTH WAYS R SUPPORTD AN IZ TOTALLY UP 2 U WHICH WAN U WANTS 2 CHOOSE. WE RECOMMEND 2 USE HTTP HEADERS EVRYWHERE WER U CAN, AS USAGE-WIZE IZ MOAR APPROPRIATE THAN QUERY STRIN. HOWEVR, WE SUPPORT QUERY STRIN AS WELL, MAINLY CUZ OV VARIOUS LIMITASHUNS RELATD 2 REQUEST HEADERS. A GUD EXAMPLE INCLUDEZ LACK OV CUSTOM HEADERS WHILE INITIATIN WEBSOCKET CONNECSHUN IN JAVASCRIPT (EVEN THOUGH IZ COMPLETELY VALID ACCORDIN 2 TEH RFC). IN DIS SITUASHUN QUERY STRIN IZ TEH ONLY WAI 2 AUTHENTICATE.
R IPC INTERFACE, IN ADDITON 2 ASF API AN ASF-UI ALSO INCLUDEZ SWAGGR DOCUMENTASHUN, WHICH IZ AVAILABLE UNDR /swagger URL. SWAGGR DOCUMENTASHUN SERVEZ AS MIDDLE-MAN TWEEN R API IMPLEMENTASHUN AN OTHR TOOLS USIN IT (E.G. ASF-UI). IT PROVIDEZ COMPLETE DOCUMENTASHUN AN AVAILABILITY OV ALL API ENDPOINTS IN OPENAPI SPECIFICASHUN DAT CAN BE EASILY CONSUMD BY OTHR PROJECTS, ALLOWIN U 2 RITE AN TEST ASF API WIF EASE.
APART FRUM USIN R SWAGGR DOCUMENTASHUN AS COMPLETE SPECIFICASHUN OV ASF API, U CAN ALSO USE IT AS USR-FRIENDLY WAI 2 EXECUTE VARIOUS API ENDPOINTS, MAINLY DOSE DAT R NOT IMPLEMENTD BY ASF-UI. SINCE R SWAGGR DOCUMENTASHUN IZ GENERATD AUTOMATICALLY FRUM ASF CODE, U HAS GUARANTEE DAT TEH DOCUMENTASHUN WILL ALWAYS BE UP-2-DATE WIF TEH API ENDPOINTS DAT UR VERSHUN OV ASF INCLUDEZ.
ASF BY DEFAULT LISTENS ONLY ON localhost ADDRESEZ, WHICH MEANZ DAT ACCESIN ASF IPC FRUM ANY OTHR MACHINE BUT UR OWN IZ IMPOSIBLE. UNLES U MODIFY DEFAULT ENDPOINTS, ATTACKR WUD NED DIRECT ACCES 2 UR OWN MACHINE IN ORDR 2 ACCES ASFS IPC, THEREFORE IZ AS SECURE AS IT CAN BE AN THAR IZ NO POSIBILITY OV ANYBODY ELSE ACCESIN IT, EVEN FRUM UR OWN LAN.
HOWEVR, IF U DECIDE 2 CHANGE DEFAULT localhost BIND ADDRESEZ 2 SOMETHIN ELSE, DEN URE SUPPOSD 2 SET PROPR FIREWALL RULEZ YOURSELF IN ORDR 2 ALLOW ONLY AUTHORIZD IPS 2 ACCES ASFS IPC INTERFACE. IN ADDISHUN 2 DOIN DAT, U WILL NED 2 SET UP IPCPassword, AS ASF WILL REFUSE 2 LET OTHR MACHINEZ ACCES ASF API WITHOUT WAN, WHICH ADDZ ANOTHR LAYR OV EXTRA SECURITY. U CUD ALSO WANTS 2 RUN ASFS IPC INTERFACE BEHIND REVERSE PROXY IN DIS CASE, WHICH IZ FURTHR EXPLAIND BELOW.
YEZ, DIS AR TEH WUT ASF API WUZ DESIGND 4 AN U CAN USE ANYTHIN CAPABLE OV SENDIN HTTP REQUEST 2 ACCES IT. LOCAL USERSCRIPTS FOLLOW CORS LOGIC, AN WE ALLOW ACCES FRUM ALL ORIGINS 4 THEM (*), AS LONG AS IPCPassword IZ SET, AS AN EXTRA SECURITY MEASURE. DIS ALLOWS U 2 EXECUTE VARIOUS AUTHENTICATD ASF API REQUESTS, WITHOUT ALLOWIN POTENTIALLY MALISHUS SCRIPTS 2 DO DAT AUTOMATICALLY (AS THEYD NED 2 KNOE UR IPCPassword 2 DO DAT).
YEZ, WE RECOMMEND 2 USE REVERSE PROXY 4 DAT. DIS WAI U CAN ACCES UR WEB SERVR IN TYPICAL WAI, WHICH WILL DEN ACCES ASFS IPC ON TEH SAME MACHINE. ALTERNATIVELY, IF U DOAN WANTS 2 RUN WIF REVERSE PROXY, U CAN USE CUSTOM CONFIGURASHUN WIF APPROPRIATE URL 4 DAT. 4 EXAMPLE, IF UR MACHINE IZ IN VPN WIF 10.8.0.1 ADDRES, DEN U CAN SET http://10.8.0.1:1242 LISTENIN URL IN IPC CONFIG, WHICH WUD ENABLE IPC ACCES FRUM WITHIN UR PRIVATE VPN, BUT NOT FRUM ANYWHERE ELSE.
YEZ, R IPC IZ FULLY COMPATIBLE WIF SUCH SETUP, SO URE FREE 2 HOST IT ALSO IN FRUNT OV UR OWN TOOLS 4 EXTRA SECURITY AN COMPATIBILITY, IF UD LIEK 2. IN GENERAL ASFS KESTREL HTTP SERVR IZ VRY SECURE AN POSESSEZ NO RISK WHEN BEAN CONNECTD DIRECTLY 2 TEH INTERNET, BUT PUTTIN IT BEHIND REVERSE-PROXY SUCH AS APACHE OR NGINX CUD PROVIDE EXTRA FUNCSHUNALITY DAT WOULDNT BE POSIBLE 2 ACHIEVE OTHERWIZE, SUCH AS SECURIN ASFS INTERFACE WIF BASIC AUTH.
EXAMPLE NGINX CONFIGURASHUN CAN BE FINDZ BELOW. WEVE INCLUDD FULL server BLOCK, ALTHOUGH URE INTERESTD MAINLY IN location ONEZ. PLZ REFR 2 NGINX DOCUMENTASHUN IF U NED FURTHR EXPLANASHUN.
server {
listen *:443 ssl;
server_name asf.mydomain.com;
ssl_certificate /path/to/your/certificate.crt;
ssl_certificate_key /path/to/your/certificate.key;
location ~* /Api/NLog {
proxy_pass http://127.0.0.1:1242;
# Only if you need to override default host
# proxy_set_header Host 127.0.0.1;
# X-headers should always be specified when proxying requests to ASF
# They're crucial for proper identification of original IP, allowing ASF to e.g. ban the actual offenders instead of your nginx server
# Specifying them allows ASF to properly resolve IP addresses of users making requests - making nginx work as a reverse proxy
# Not specifying them will cause ASF to treat your nginx as the client - nginx will act as a traditional proxy in this case
# If you're unable to host nginx service on the same machine as ASF, you most likely want to set KnownNetworks appropriately in addition to those
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Server $host;
# We add those 3 extra options for websockets proxying, see https://nginx.org/en/docs/http/websocket.html
proxy_http_version 1.1;
proxy_set_header Connection "Upgrade";
proxy_set_header Upgrade $http_upgrade;
}
location / {
proxy_pass http://127.0.0.1:1242;
# Only if you need to override default host
# proxy_set_header Host 127.0.0.1;
# X-headers should always be specified when proxying requests to ASF
# They're crucial for proper identification of original IP, allowing ASF to e.g. ban the actual offenders instead of your nginx server
# Specifying them allows ASF to properly resolve IP addresses of users making requests - making nginx work as a reverse proxy
# Not specifying them will cause ASF to treat your nginx as the client - nginx will act as a traditional proxy in this case
# If you're unable to host nginx service on the same machine as ASF, you most likely want to set KnownNetworks appropriately in addition to those
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Server $host;
}
}EXAMPLE APACHE CONFIGURASHUN CAN BE FINDZ BELOW. PLZ REFR 2 APACHE DOCUMENTASHUN IF U NED FURTHR EXPLANASHUN.
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName asf.mydomain.com
SSLEngine On
SSLCertificateFile /path/to/your/fullchain.pem
SSLCertificateKeyFile /path/to/your/privkey.pem
# TODO: APACHE CANT DO CASE-INSENSITIV MATCHIN PROPERLY, SO WE HARDCODE 2 MOST COMMONLY USD CASEZ
ProxyPass "/api/nlog" "ws://127.0.0.1:1242/api/nlog"
ProxyPass "/Api/NLog" "ws://127.0.0.1:1242/Api/NLog"
ProxyPass "/" "http://127.0.0.1:1242/"
</VirtualHost>
</IfModule>YEZ, U CAN ACHIEVE IT THRU 2 DIFFERENT WAYS. A RECOMMENDD WAI WUD BE 2 USE REVERSE PROXY 4 DAT, WER U CAN ACCES UR WEB SERVR THRU HTTPS LIEK USUAL, AN CONNECT THRU IT WIF ASFS IPC INTERFACE ON TEH SAME MACHINE. DIS WAI UR TRAFFIC IZ FULLY ENCRYPTD AN U DOAN NED 2 MODIFY IPC IN ANY WAI 2 SUPPORT SUCH SETUP.
SECOND WAI INCLUDEZ SPECIFYIN CUSTOM CONFIG 4 ASFS IPC INTERFACE WER U CAN ENABLE HTTPS ENDPOINT AN PROVIDE APPROPRIATE CERTIFICATE DIRECTLY 2 R KESTREL HTTP SERVR. DIS WAI IZ RECOMMENDD IF URE NOT RUNNIN ANY OTHR WEB SERVR AN DOAN WANTS 2 RUN WAN EXCLUSIVELY 4 ASF. OTHERWIZE, IZ MUTCH EASIR 2 ACHIEVE SATISFYIN SETUP BY USIN REVERSE PROXY MECHANISM.
DURIN STARTUP OV IPC IM GETTIN AN ERROR: System.IO.IOException: Failed to bind to address, An attempt was made to access a socket in a way forbidden by its access permissions
DIS ERROR INDICATEZ DAT SOMETHIN ELSE ON UR MACHINE IZ EITHR ALREADY USIN DAT PORT, OR RESERVD IT 4 FUCHUR USE. DIS CUD BE U IF URE ATTEMPTIN 2 RUN SECOND ASF INSTANCE ON TEH SAME MACHINE, BUT MOST OFTEN THAZ WINDOWS EXCLUDIN PORT 1242 FRUM UR USAGE, THEREFORE ULL HAS 2 MOOV ASF 2 ANOTHR PORT. IN ORDR 2 DO DAT, FOLLOW EXAMPLE CONFIG ABOOV, AN SIMPLY TRY 2 PICK ANOTHR PORT, SUCH AS 12420.
OV COURSE U CUD ALSO TRY 2 FIND OUT WUT IZ BLOCKIN PORT 1242 FRUM ASF USAGE, AN REMOOV DAT, BUT THAZ USUALLY FAR MOAR TROUBLESOME THAN SIMPLY INSTRUCTIN ASF 2 USE ANOTHR PORT, SO WELL SKIP ELABORATIN FURTHR ON DAT HER.
ASF INCLUDEZ ADDISHUNAL SECURITY MEASURE DAT, BY DEFAULT, ALLOWS ONLY LOOPBACK INTERFACE (localhost, UR OWN MACHINE) 2 ACCES ASF API WITHOUT IPCPassword SET IN DA CONFIG. DIS AR TEH CUZ USIN IPCPassword SHUD BE MINIMUM SECURITY MEASURE SET BY EVRYBODY HOO DECIDEZ 2 EXPOSE ASF INTERFACE FURTHR.
TEH CHANGE WUZ DICTATD BY TEH FACT DAT MASIF AMOUNT OV ASFS HOSTD GLOBALLY BY UNAWARE USERS WUZ BEAN TAKEN OVAR 4 MALISHUS INTENTS, USUALLY LEAVIN PEEPS WITHOUT ACCOUNTS AN WITHOUT ITEMS ON THEM. NAO WE CUD SAY "THEY CUD READ DIS PAEG BEFORE OPENIN ASF 2 TEH ENTIRE WURLD", BUT INSTEAD IT MAKEZ MOAR SENSE 2 DISALLOW INSECURE ASF SETUPS BY DEFAULT, AN REQUIRE FRUM USERS AN ACSHUN IF THEY EXPLICITLY WANTS 2 ALLOW IT, WHICH WE ELABORATE BOUT BELOW.
IN PARTICULAR, URE ABLE 2 OVERRIDE R DECISHUN BY SPECIFYIN TEH NETWORKZ WHICH U TRUST 2 REACH ASF WITHOUT IPCPassword SPECIFID, U CAN SET DOSE IN KnownNetworks PROPERTY IN CUSTOM CONFIG. HOWEVR, UNLES U RLY KNOE WUT URE DOIN AN FULLY UNDERSTAND TEH RISKZ, U SHUD INSTEAD USE IPCPassword AS DECLARIN KnownNetworks WILL ALLOW EVRYBODY FRUM DOSE NETWORKZ 2 ACCES ASF API UNCONDISHUNALLY. WERE SERIOUS, PEEPS WUZ ALREADY SHOOTIN THEMSELVEZ IN DA FOOT BELIEVIN THEIR REVERSE PROXIEZ AN IPTABLEZ RULEZ WUZ SECURE, BUT THEY WUZ NOT, IPCPassword IZ TEH FURST AN SOMETIMEZ TEH LAST GUARDIAN, IF U DECIDE 2 OPT OUT OV DIS SIMPLE, YET VRY EFFECTIV AN SECURE MECHANISM, ULL HAS ONLY YOURSELF 2 BLAME.
 |
 |
 |
 |
|---|---|---|---|
 |
 |
 |
 |
|---|---|---|---|
- 🏡 HOME
- 🔧 CONFIGURASHUN
- 💬 FAQ
- ⚙️ SETTIN UP (START HER)
- 👥 BAKGROUND GAMEZ REDEEMR
- 📢 COMMANDZ
- 🛠️ COMPATIBILITY
- 🧩 ITEMSMATCHERPLUGIN
- 📋 MANAGEMENT
- ⏱️ PERFORMANCE
- 📡 REMOTE COMMUNICASHUN
- 👪 STEAM PPLZ SHARIN
- 🔄 TRADIN

